Onion routing
Onion routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which "peels" away a single layer, uncovering the data's next destination. When the final layer is decrypted, the message arrives at its destination. The sender remains anonymous because each intermediary knows only the location of the immediately preceding and following nodes.[1]
Development and implementation
Onion routing was developed in the mid-1990s at the U.S. Naval Research Laboratory by employees Paul Syverson, Michael G. Reed, and David Goldschlag[2][3] to protect U.S. intelligence communications online.[4] It was further developed by the Defense Advanced Research Projects Agency (DARPA) and patented by the Navy in 1998.[3][5][6]
Computer scientists Roger Dingledine and Nick Mathewson joined Syverson in 2002 to develop what would become the largest and best known implementation of onion routing, Tor, then called The Onion Routing project or TOR project. After the Naval Research Laboratory released the code for Tor under a free license,[4][7][8] Dingledine, Mathewson and five others founded The Tor Project as a non-profit organization in 2006, with the financial support of the Electronic Frontier Foundation and several other organizations.[9][10]
Data structure
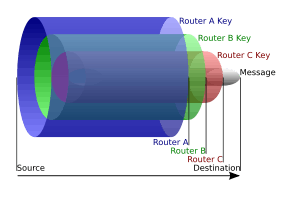
An onion is the data structure formed by "wrapping" a message with successive layers of encryption to be decrypted ("peeled" or "unwrapped") by as many intermediary computers as there are layers before arriving at its destination. The original message remains hidden as it is transferred from one node to the next, and no intermediary knows both the origin and final destination of the data, allowing the sender to remain anonymous.[11]
Onion creation and transmission
To create and transmit an onion, the originator selects a set of nodes from a list provided by a "directory node". The chosen nodes are arranged into a path, called a "chain" or "circuit", through which the message will be transmitted. To preserve the anonymity of the sender, no node in the circuit is able to tell whether the node before it is the originator or another intermediary like itself. Likewise, no node in the circuit is able to tell how many other nodes are in the circuit and only the final node, the "exit node", is able to determine its own location in the chain.[11]
Using asymmetric key cryptography, the originator obtains a public key from the directory node to send an encrypted message to the first ("entry") node, establishing a connection and a shared secret ("session key"). Using the established encrypted link to the entry node, the originator can then relay a message through the first node to a second node in the chain using encryption that only the second node, and not the first, can decrypt. When the second node receives the message, it establishes a connection with the first node. While this extends the encrypted link from the originator, the second node cannot determine whether the first node is the originator or just another node in the circuit. The originator can then send a message through the first and second nodes to a third node, encrypted such that only the third node is able to decrypt it. The third, as with the second, becomes linked to the originator but connects only with the second. This process can be repeated to build larger and larger chains, but is typically limited to preserve performance.[11]
When the chain is complete, the originator can send data over the Internet anonymously. When the final recipient of the data sends data back, the intermediary nodes maintain the same link back to the originator, with data again layered, but in reverse such that the final node this time removes the first layer of encryption and the first node removes the last layer of encryption before sending the data, for example a web page, to the originator.[11]
Weaknesses
Timing analysis
One of the reasons typical Internet connections are not considered anonymous is the ability of Internet service providers to trace and log connections between computers. For example, when a person accesses a particular website, the data itself may be secured through a connection like HTTPS such that your password, emails, or other content is not visible to an outside party, but there is a record of the connection itself, what time it occurred, and the amount of data transferred. Onion routing creates and obscures a path between two computers such that there's no discernible connection directly from a person to a website, but there still exist records of connections between computers. Traffic analysis searches those records of connections made by a potential originator and tries to match timing and data transfers to connections made to a potential recipient. For example, a person may be seen to have transferred exactly 51 kilobytes of data to an unknown computer just three seconds before a different unknown computer transferred exactly 51 kilobytes of data to a particular website.[12][13] Factors that may facilitate traffic analysis include nodes failing or leaving the network[13] and a compromised node keeping track of a session as it occurs when chains are periodically rebuilt.[14]
Garlic routing is a variant of onion routing associated with the I2P network that encrypts multiple messages together to make it more difficult[15] for attackers to perform traffic analysis and to increase the speed of data transfer.[16]
Exit node vulnerability
Although the message being sent is transmitted inside several layers of encryption, the job of the exit node, as the final node in the chain, is to decrypt the final layer and deliver the message to the recipient. A compromised exit node is thus able to acquire the raw data being transmitted, potentially including passwords, private messages, bank account numbers, and other forms of personal information. Dan Egerstad, a Swedish researcher, used such an attack to collect the passwords of over 100 email accounts related to foreign embassies.[17]
Exit node vulnerabilities are similar to those on unsecured wireless networks, where the data being transmitted by a user on the network may be intercepted by another user or by the router operator. Both issues are solved by using a secure end-to-end connection like SSL or secure HTTP (S-HTTP). If there is end-to-end encryption between the sender and the recipient, then not even the last intermediary can view the original message.
See also
- Bitblinder
- Chaum mixes
- Cryptography
- Degree of anonymity
- Diffie–Hellman key exchange
- Java Anon Proxy
- Matryoshka doll
- Proxy server
- Tox – implements onion routing
- Tribler – implements onion routing
References
- ↑ Goldschlag D., Reed M., Syverson P. (1999.) Onion Routing for Anonymous and Private Internet Connections, Onion Router.
- ↑ Reed M. G., Sylverson P. F., Goldschlag D. M. (1998) "Anonymous connections and onion routing", IEEE Journal on Selected Areas in Communications, 16(4):482-494.
- 1 2 US patent 6266704, Reed; Michael G. (Bethesda, MD), Syverson; Paul F. (Silver Spring, MD), Goldschlag; David M. (Silver Spring, MD), "Onion routing network for securely moving data through communication networks", assigned to The United States of America as represented by the Secretary of the Navy (Washington, DC)
- 1 2 Levine, Yasha (16 July 2014). "Almost everyone involved in developing Tor was (or is) funded by the US government". Pando Daily. Retrieved 30 August 2014.
- ↑ Fagoyinbo, Joseph Babatunde (2013-05-24). The Armed Forces: Instrument of Peace, Strength, Development and Prosperity. AuthorHouse. ISBN 9781477226476. Retrieved August 29, 2014.
- ↑ Leigh, David; Harding, Luke (2011-02-08). WikiLeaks: Inside Julian Assange's War on Secrecy. PublicAffairs. ISBN 1610390628. Retrieved August 29, 2014.
- ↑ Dingledine, Roger (20 September 2002). "pre-alpha: run an onion proxy now!". or-dev (Mailing list). Retrieved 17 July 2008.
- ↑ "Tor FAQ: Why is it called Tor?". Tor Project. Retrieved 1 July 2011.
- ↑ "Tor: Sponsors". Tor Project. Retrieved 11 December 2010.
- ↑ Krebs, Brian (8 August 2007). "Attacks Prompt Update for 'Tor' Anonymity Network". Washington Post. Retrieved 27 October 2007.
- 1 2 3 4 Roger Dingledine; Nick Mathewson; Paul Syverson. "Tor: The Second-Generation Onion Router" (PDF). Retrieved 26 February 2011.
- ↑ Shmatikov, Wang; Ming-Hsiu Vitaly (2006). "Timing analysis in low-latency mix networks: attacks and defenses". Proceedings of the 11th European conference on Research in Computer Security. ESORICS'06: 18–33. doi:10.1007/11863908_2. Retrieved 24 October 2012.
- 1 2 Dingledine, Roger. "Tor: The Second-Generation Onion Router". Tor Project. Retrieved 24 October 2012.
- ↑ Wright, Matthew. K.; Adler, Micah; Levine, Brian Neil; Shields, Clay (November 2004). "The Predecessor Attack: An Analysis of a Threat to Anonymous Communications Systems" (PDF). ACM Transactions on Information and System Security. 7 (4): 489–522. doi:10.1145/1042031.1042032.
- ↑ http://privacy-pc.com/articles/common-darknet-weaknesses-2-tor-and-i2p.html
- ↑ Zantour, Bassam; Haraty, Ramzi A. (2011). "I2P Data Communication System". Proceedings of ICN 2011: The Tenth International Conference on Networks. IARIA: 401–409.
- ↑ Bangeman, Eric (2007-08-30). "Security researcher stumbles across embassy e-mail log-ins". Arstechnica.com. Retrieved 2010-03-17.
External links
- Onion-Router.net - site formerly hosted at the Center for High Assurance Computer Systems of the U.S. Naval Research Laboratory
- Sylverson, P. F.; Goldschlag, D. M.; Reed, M. G. (1997). "Anonymous Connections and Onion Routing". IEEE Symposium on Security and Privacy. CiteSeerx: 10.1.1.64.4829 - The original paper from the Naval Research Laboratory