Key feedback mode
In cryptography key feedback mode (KFB) is a mode of operation for cryptographic block ciphers. It uses the block cipher output block to form the block cipher key of the next round, thereby creating a keystream generator that can be used as a synchronous stream cipher.
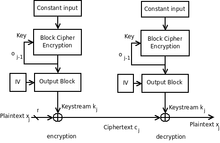
Operation
KFB mode outputs m bits (typically m = 8) at a time and uses a constant bitstring p as block cipher input, a key k of n bit length, and a n × m matrix with non-zero rows as IV. It is possible to reduce the size of the matrix and it does not need to be secret but must be random. If the output block size of the block cipher is not equal to the key size, a function is needed to form a valid key from the output block. The speed of KFB is a bit lower than for other modes of operation like OFB, mainly because the key schedule has to be done for each key.
Security
Hastad and Näslund proved KFB to be secure in terms of the theorems of complexity theory introduced by Blum, Micali, Levin and Goldreich, giving a quantitative relation between the effort of distinguishing the keystream from true randomness to the effort of retrieving the secret key.
Error properties
As the keystream is independent of plaintext and ciphertext, KFB mode turns a block cipher into a synchronous stream cipher. Just as with other synchronous stream ciphers, inverting a bit in the ciphertext produces an inverted bit in the plaintext at the same location, but does not affect further parts of the plaintext. This property allows many error correcting codes to function normally even when applied before encryption.
History
The concept of KFB has already been mentioned 1982 by Hellman and Reyneri,[1] but only as a theoretical construct to analyse the cycle length of random functions with the purpose of comparing DES to a truly random function. The detailed specification was published and submitted to NIST in 2000 by J. Håstad and M. Naslund.
References
- ↑ Martin E. Hellman and Justin M. Reyneri. Drainage and the DES. In Advances in Cryptology: Proceedings of Crypto 82, pages 129–131, 1982