Communication privacy management theory
Communication privacy management (CPM), originally known as communication boundary management, is a theory about how people make decisions about revealing and concealing private information. CPM theory suggests that individuals maintain and coordinate privacy boundaries (the limits of what they are willing to share) with various communication partners depending on the perceived benefits and costs of information disclosure. It was first developed by Sandra Petronio in 1991.
Petronio uses a boundary metaphor to explain the privacy management process. Privacy boundaries draw divisions between private information and public information. This theory argues that when people disclose private information, they depend on a rule-based management system to control the level of accessibility. An individual’s privacy boundary governs his or her self-disclosures. Once a disclosure is made, the negotiation of privacy rules between the two parties is required. A distressing sense of “boundary turbulence” can arise when clashing expectations for privacy management are identified. Having the mental image of protective boundaries is central to understanding the five core principles of Petronio’s CPM:
(1) People believe they own and have a right to control their private information. (2) People control their private information through the use of personal privacy rules. (3) When others are told or given access to a person’s private information, they become co-owners of that information. (4) Co-owners of private information need to negotiate mutually agreeable privacy rules about telling others. (5) When co-owners of private information don’t effectively negotiate and follow mutually held privacy rules, boundary turbulence is the likely result.
Background
Petronio’s communication privacy management (CPM) theory is built on Altman’s dialectical conception of privacy as a process of opening and closing a boundary to others.[1] Altman and Taylor’s social penetration theory focused on self-disclosure as the primary way to develop close relationships. However, openness is only part of the story. We also have a desire for privacy. When Petronio first developed this theory in 1991, it was called communication boundary management. In 2002, she renamed it to communication privacy management, underscoring private disclosure is the main thrust of the theory.
Theory elements
Private information
The content of concealing and revealing is private information. Petronio favored the term "private information" over the term "self-disclosure" because there are many caveats inherent to private information disclosure that are not present with self-disclosure.[2] Firstly, the motivations behind sharing are many, including but not limited to: sharing a burden, righting a wrong, and influencing others.[3] Since private information can be about yourself or others, the decision as to what is private and whom to share it with plays a part when taking the idea of boundaries into consideration.[4] The decision to share is ultimately left up to the process of the privacy rule management system which combines rules for coordination of information, characteristics of disclosure, and attributes of the nature of boundaries.
Private boundaries
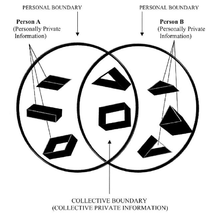
To understand CPM theory it is important to follow the metaphor of the boundary. Private boundaries are the division between private information and public information.[5] When private information is shared, there will be a collective boundary. When private information remains with an individual and is not disclosed, the boundary is called a personal boundary. An individual’s private information is protected by their boundaries. The permeability of these boundaries are ever-changing. Boundaries can be relatively permeable (easy to cross) or relatively impregnable (rigid and difficult to cross).
Control and ownership
Communication privacy management theory understands information (as well as boundaries) as something that is owned, and each owner must decide whether or not they are willing to have a confidant, i.e. a co-owner, to that information. In some cases, it is preferable for the owner to have another person share the private information, though this may not be the case for the confidant. Co-ownership of information is characterized by two things: heavy responsibility and a knowledge of the rules for a particular disclosure. However, ownership can be felt to different degrees, and the understanding of disclosure rules can be different from owner to owner. Also, the act of sharing is coupled along with the realization that boundaries have expanded and that they may never return to their original state. It is the responsibility of co-owners to decide and make clear if, when, and how information can or should be shared with others.[6]
Rule-based management system

As the framework for understanding the decisions people make about private information, this system allows for management on the individual and collective levels through three processes: privacy rule characteristics, boundary coordination, and boundary turbulence.
Management dialectics
Petronio's understanding and argument of privacy management rests on the idea that a dialectic exists wherever the decision is made to disclose or conceal private information. Thus, costs and benefits must be weighed and consideration must be given to how such information will be owned, used, and spread.[7] The definition of dialectic that Petronio borrows from can be found in Leslie Baxter and Barbara Montgomery's theory of relational dialectics, wherein various approaches to the contradictory impulses of relational life are discussed. The theory focuses on the idea that there are not only two contradictory stances within a relationship, but that at any given moment decisions are weighed using multiple viewpoints.[8]
Rule-based management system
Petronio views boundary management as a rule based process, not an individual decision. This rule-based management system allows for management on the individual and collective levels. This system depends on three privacy rule management to regulate the process of revealing and concealing private information: privacy rule characteristics, boundary coordination, and boundary turbulence.
Privacy rule characteristics
The characteristics of privacy rules are divided into two sections, attributes and development. Privacy rule attributes refer to how people obtain rules of privacy and understand the properties of those rules.[9] This is normally done through social interactions where the boundaries for rules are put to the test. Rules are set in different social situations which dictate the type of disclosure that should be made, for example, the difference between disclosure at a family member's birthday party versus an office event at work. Petronio asserts that each situation will come with its own set of rules for managing privacy that are learned over time. The development of privacy rule characteristics has to do with the criteria implemented to decide if and how information will be shared.[10] Communication privacy management theory general lists those criteria as the following:
|
Decision Criteria |
Category |
Definition |
Example |
|---|---|---|---|
| Cultural | core | Disclosure depends on the norms for privacy and openness in a given culture. | The United States favors more openness in relational communication than does Japan |
| Gender | core | Privacy boundaries are sculpted differently by men and women based on socialization, which leads to difference in how rules are understood and operated in | American women are socialized to be more disclosive than men |
| Contextual | catalyst | Shaped by issues of physical and social environments that factor in whether or not information will be shared | If we’re in a traumatic situation (e.g., we’ve survived an earthquake together), we’ll develop new rules |
| Motivational | catalyst | Owners of information can form certain bonds that lead to disclosure, or conversely the express interest in forming bonds may cause private information to be shared. Motivations for sharing can include reciprocity or self-clarification. | If you have disclosed a great deal to me, out of reciprocity, I might be motivated to disclose to you |
| Risk-benefit | catalyst | Owners of private information evaluate risks relative to the benefits of disclosure or maintaining information private. | Our rules are influenced by our assessment of the ratio of risks to benefits of disclosing |
With these five criteria, personal and group privacy rules are developed, but disclosure of private information necessitates the inclusion of others within the boundary of knowledge, which demands an understanding between parties for how to coordinate ownership of knowledge.
Boundary coordination
An individual’s private information is protected by the individual’s boundaries. The permeability of these boundaries are ever changing, and allow certain parts of the public, access to certain pieces of information belonging to the individual. Once private information is shared, co-owners must coordinate the boundaries of privacy and disclosure based on boundary permeability, boundary linkage, and boundary ownership.[9] Petronio describes this mutual boundary coordination by co-owners as drawing the same borders on a map around a shared piece of information.[10] By no means is this an easy process considering that each owner will approach the information from distinct viewpoints and referencing their personal criteria for privacy rule development.
- Boundary permeability refers to the nature of the invisible divisions that keep private information from being known outside of an individual or particular group. When private information is kept with one owner, the boundaries are said to be thick because there is less possibility for information to make its way out into the public sphere. Once information is shared to one or more persons, the boundaries for that private information expand, become more permeable, and are considered thin.[6]
- Boundary linkage has to do with how owners are connected when they build associations through a boundary. For example, doctors and patients are linked to each other in such a way that private information is passed within their boundaries constantly. These linkages can be strong or weak depending on how information was shared or whether a co-owner wanted to know or was prepared to learn a new piece of information. Case in point, the link between an organization and a spy meant to infiltrate the organization is weak because the two are not coordinated on how information will be maintained private or disclosed.[11]
- Boundary ownership refers to the responsibilities and rights each person has over the control of the spread of information that they own. When working to mutually create the boundary of privacy it is key for all parties to have a clear understanding of whether information should be shared, who it should be shared with, and when it should be shared.[9] A simple example of this is the planning of a surprise birthday party; all those involved in planning must agree on how the information about the party will be spread so as not to ruin the surprise. As new guests are invited, they become an owner of the information and are bound to the rules of privacy maintenance, or else the surprise could be ruined.
Boundary turbulence
Often, boundaries are not coordinated as well as they should be to maintain the level of privacy or exposure desired by owners – this leads to problems known as boundary turbulence. The coordination of shared boundaries is key to avoiding over-sharing. When the boundaries are unclear, owners may come into conflict with one another. Turbulence among co-owners is caused when rules are not mutually understood by co-owners and when the management of private information comes into conflict with the expectations each owner had,[2] which can happen for a number of reasons.
Boundary turbulence can be caused by mistakes, such as an uninvited party overhearing private information (causing weak boundary linkage) or a disclosure an owner might make under the influence of alcohol or other drugs. Disclosure to a new party was not the intent, but, when it happens, other co-owners can feel that their expectations of maintaining boundaries have been violated.
In addition, boundary turbulence occurs when a co-owner intentionally breaks the coordinated boundary of privacy to disclose private information.[12] An example of such intentional disclosure would be a daughter revealing to a doctor that her father is indeed an active smoker when the father has told the doctor that he no longer smokes after his heart surgery. The daughter in this case must weigh the risks of breaking the family privacy boundary against the benefits of the doctor being better informed of her father's condition.
Lastly, boundary turbulence can also occur when there have not been pre-existing rules for a situation. For example, with the emergence of Social media and, in particular, Facebook, boundary rules had not been established. As parents began to join Facebook and "friend" their children, the children felt turbulence. There was a perception of privacy invasion between the parent-child relationship.[13]
In cases of boundary turbulence, co-owners of information can feel that their expectations have been violated and lose trust in other co-owners. In these cases, the goal of each party is to reduce turbulence by reestablishing and coordinating boundaries.[5][12] It should be noted, however, that turbulence doesn't always have a negative outcome, there has been studies which show that turbulence within relationships can lead to stronger and improved relationships.[14]
Theory applications
Communication privacy management can be applied across different contexts, primarily include: (1) family communication, with a particular focus on parental privacy invasions, (2) online social media, (3) health, and (4) relational issues,[15] and (5) work environments.[16]
Family communication
Specific applications of CPM highlight family privacy management. Research focused on secrets and topic avoidance, such as questions of concealment to stepfamily members feeling caught, and parents-adolescent conversations about sex.[17] Family privacy research over the decades are also inspired specifically by the chapter of parental privacy invasion. For example, work by Hawk and his colleagues explore perceived parental invasions from the view of adolescents in reaction to such issues as control attempts, solicitation of information, and conflict outcomes.[18] Another way that family communication uses CPM is with child bearing or the lack thereof; whom childless-couples choose to disclose to that they voluntarily do not want children is another way CPM has been explored.[19]
Online social media
Recent researchers apply CPM to investigate privacy management for online blogging, Facebook usage and online dating. Further, there have been investigations into parental behavior that is enacted through online social media; specifically when parents 'friend' their children and the management of privacy that ensues from that.[20] Privacy practices in social network sites often appear paradoxical, as content-sharing behavior stands in conflict with the need to reduce disclosure-related harms. Some study explore privacy in social network sites as a contextual information practice, managed by a process of boundary regulation.[21]
Health communication
Informed by principles of CPM, health communication research using CPM to explore health privacy issues has become a growth area. Earlier study investigated physician disclosure of medical mistakes. Recently there have been a number of studies focused on ways that privacy issues influence patient care, confidentiality and control over ownership, choices about disclosure, for instance, with stigma health-related illness such as HIV/AIDS , about e-health information, and the digitization of healthcare.
Relationship issues
Many studies emphasize the use of CPM in relationships because of the concepts of disclosure and boundaries. Not only romantic relationships, but also friendships are a factor when thinking of CPM.[22] Briefly, work on conflict and topic avoidance, considering the relational impact of privacy turbulence , students and faculty relationships, and workplace relationships have all produced useful information that opens new doors regarding CPM-based research.
Work environments
CPM has become very applicable in the workplace as personal mobile devices have increasingly been allowed to be brought to work. The concept of Bring Your Own Device (BYOD) has stirred conversation on the concept of privacy, security and boundaries between employee and employer. Companies have had to take measures to further secure their network or even decide whether they want to have employee access personal accounts (i.e. email) or devices while on the job. By the same token, some employees argue that companies should not be able to track what is being done on their personal devices or even on company computers even if they are in the work place.[23][24] Even before stepping foot into the workplace, much can be said about CPM and interviewing. How much we decide to reveal within an interview and the boundaries we have in that situation is directly related to CPM.[25] Even interviewing within a job (as a cop, for example) requires a certain sensitivity to people's boundaries and how much private information they are willing to reveal.[26]
Related theories
There are a few communication theories that are worth noting after understanding CPM in more depth.
Expectancy violations theory discusses the importance of personal space, territoriality and the expectations individuals have of another's non verbal communication. Though dealing with physical proximity, we can see the relation between expectancy violations theory and CPM as it pertains to privacy and how close we allow another to come to us. Both physical and intimate proximity requires boundaries to be crossed or permeated.
Social penetration theory explains how two individuals grow in intimacy and move from one level to the next in their relationships. The popular idea behind social penetration is that individual are like onions; they have layers and as you go deeper, the more intimate you become. For this intimacy to occur, we can safely say that private information needs to shared and exchanged. As one does this, boundaries are permeated and become co-owned.
Finally, coordinated management of meaning explains how people establish rules for both creating and interpreting meaning. Similar to CPM, coordinated management of meaning has stages were coordination is achieved, not achieved, or partially achieved. Similarly you can have boundary ownership, boundary turbulence or boundary linkage. Moreover, in order to achieve meaning there needs to be an exchange of information between individuals to decipher. This exchange of private information falls directly into CPM.
Critique
Values
Altman speaks to the values of this theory as it advances our thinking by incorporating different “levels” or combinations of participants in communication processes (Altman 2002). Whereas earlier research and theorizing on privacy-disclosure focused on dyads or individuals, a most complicated set of dynamics has been carefully enunciated by Petronio. Petronio also describes communication within families and between family members and outsiders, within and outside work and social groups, and between many combinations of individuals, dyads, and others within and across social boundaries. In addition, her analysis of privacy-disclosure “turbulence,” or breaches of desired communication patterns, is articulate and systematic.[12][27][28]
Criticism
Some researchers have questioned whether CPM theory truly is dialectical in nature. It has argued that CPM takes a dualistic approach, treating privacy and disclosure as independent of one another and able to coexist in tandem rather than in the dynamic interplay characteristic of dialectics. This accusation of dualistic thinking might result from the theory's use of the terms balance and equilibrium in the early versions of CPM theory. Petronio argues that CPM is not focused on balance in the psychological sense. "Instead, [CPM] argues for coordination with others that does not advocate an optimum balance between disclosure and privacy. As an alternative, the theory claims there are shifting forces with a range of privacy and disclosure that people handle by making judgments about the degrees [emphasis in original] of privacy and publicness they wish to experience in any given interaction" (pp. 12–13). Thus, Petronio argues that it is legitimate to call CPM theory dialectical in nature.
See also
References
- ↑ "Communication Privacy Management in Electronic Commerce". 2001.
- 1 2 Petronio, S. (2002). Boundaries of Privacy: Dialectics of Disclosure. Albany, NY: SUNY Press.
- ↑ Petronio, S (1991). "Communication boundary management: A theoretical model of managing disclosure of private information between married couples". Communication Theory 1: 311–335. doi:10.1111/j.1468-2885.1991.tb00023.x.
- ↑ Matthews, Alicia; Derlega, Valerien; Morrow, Jennifer (Aug 20, 2006). "What is Highly Personal Information and How Is It Related to Self-Disclosure Decision-Making?". Communication Research Reports 23 (2): 85–92. doi:10.1080/08824090600668915.
- 1 2 Petronio, S., Ellmers, N., Giles, H., Gallois, C. (1998). (Mis)communicating across boundaries: Interpersonal and intergroup considerations. Communication Research, 25, 571–595.
- 1 2 Petronio, S., & Durham, W.T. (2008). Communication privacy management theory. In L.A. Baxter & D.O. Braithwaite (Eds.), Engaging theories in interpersonal communication: Multiple perspectives (pp. 309-322). Thousand Oaks, CA: Sage.
- ↑ Petronio, S., & Reierson, J. (2009). Regulating the Privacy of Confidentiality: Grasping the Complexities through Communication Privacy Management Theory. Uncertainty, Information Management, and Disclosure Decisions: Theories and Applications. 365–383.
- ↑ Baxter, L.A., & Montgomery, B. (1996). Relating Dialogues and dialectics: New York: Guilford Press.
- 1 2 3 Petronio, S. (1991). Communication boundary management: A theoretical model of managing disclosure of private information between married couples. Communication Theory, 1, 311–335.
- 1 2 Petronio, S. (2007). Translational Research Endeavors and the Practices of Communication Privacy Management. Journal of Applied Communication Research, 35, 218-222.
- ↑ Caughlin, J.P.; Afifi, T.D. (2004). "When is topic avoidance unsatisfying? Examining moderators of the association between avoidance and dissatisfaction". Human Communication Research 30: 479–513. doi:10.1093/hcr/30.4.479.
- 1 2 3 Afifi, T. D. (2003). "Feeling caught" in stepfamilies: managing boundary turbulence through appropriate communication privacy rules". Journal of Social and Personal Relationships 20: 729–755. doi:10.1177/0265407503206002.
- ↑ Kanter, M.; Robbins, S. (2012). "The Impact of Parents "Friending" Their Young Adult Child on Facebook on Perceptions of Parental Privacy Invasions and Parent-Child Relationship Quality". Journal of Communication 62: 900 of 917. doi:10.1111/j.1460-2466.2012.01669.x.
- ↑ McLaren, R.M. (August 2013). "Emotions, Communicative responses, and relational consequences of boundary turbulence". Journal of Social and Personal Relationships 30 (5): 606–626. doi:10.1177/0265407512463997.
- ↑ "Brief Status Report on Communication Privacy Management Theory". Journal of Family Communication 13: 6–14. 2013. doi:10.1080/15267431.2013.743426.
- ↑ Miller, Seumas; Weckert, John (2000). "Privacy, the Workplace and the Internet". Journal of Business Ethics 28 (3): 255–65.
- ↑ Afifi, T.D. (2003). "‘Feeling caught’ in stepfamilies: Managing boundary turbulence through appropriate communication privacy rules". Journal of Social and Personal Relationships 20: 729–755. doi:10.1177/0265407503206002.
- ↑ Petronio, Sandra (2013). "Brief Status Report on Communication Privacy Management Theory". Journal of Family Communication 13: 6–14. doi:10.1080/15267431.2013.743426.
- ↑ Durham, Wesley (May 21, 2008). "The Rules-Based Process of Revaling/Concealing the Family Planning Decisions of Voluntarily Child-Free Couples: A Communication Privacy Management Perspective". Communication Studies 59 (2): 132–147.
- ↑ Kanter, Maggie; Robbins, Stephanie (October 2012). "The Impact of Parents "Friending" Their Young Adult Child on Facebook on Perceptions of Parental Privacy Invasions and Parent–Child Relationship Quality". Journal of Communication 62 (5): 900–917. doi:10.1111/j.1460-2466.2012.01669.x.
- ↑ Fred Stutzman, Jacob Kramer-Duffield (April 2010). "Friends Only: Examining a Privacy-Enhancing Behavior in Facebook".
- ↑ McBride, Chad; Bergen, Karla (2008). "Communication Research: Becoming a Reluctant Confidant: Communication Privacy Management in Close Friendships". Texas Speech Communication Journal 33 (1): 50–61.
- ↑ Miller, Seumas; Weckert, John (December 2000). "Privacy, the Workplace and the Internet". Journal of Business Ethics 28 (3): 255–265. doi:10.1023/a:1006232417265.
- ↑ Miller, K.W.; Voas, J.; Hurlburt, G.F. (Sep–Oct 2012). "BYOD: Security and Privacy Considerations". IT Professional 14 (5): 53–55. doi:10.1109/mitp.2012.93.
- ↑ Hackney, Michael; Kleiner, Brian (1994). "Conducting an Effective Selection Interview". Work Study 43 (7): 8–13. doi:10.1108/eum0000000004009.
- ↑ Powell, Martine; Wright, Rebecca; Clark, Susan (2010). "Improving the Competency of Police Officers in Conducting Investigative Interviews with Children". Police Practice & Research 11 (3): 211–226. doi:10.1080/15614260902830070.
- ↑ Petronio, S.; Martin, J.N. (1986). "Ramifications of revealing private information: A gender gap". Journal of Clinical Psychology 42: 499–506. doi:10.1002/1097-4679(198605)42:3<499::aid-jclp2270420317>3.0.co;2-i.
- ↑ Petronio, S. Martin; Littlefield, R. (1984). "Prerequisite conditions for self-disclosing: A gender issue". Communication Monographs 51: 268–273. doi:10.1080/03637758409390200.