Cloudbric
Cloudbric is a software as a service, security as a service, designed to protect websites from malicious intents. It is intended to protect against web hacking including SQL Injection, Cross-site scripting, identity theft, website defacement and application layer DDoS attack. The company is based in Houston, Texas. It offers free web security services for small and medium-sized enterprises, charging based on website traffic rather than services offered, allowing small and starting websites to access all services for free.[1]
Company Overview
Founded by Jaeson Yoo in 2014, Penta Security Systems Co. (USA) provides web application security products to more than 2,900 firms including the government, large enterprises, small and medium businesses, educational and financial organizations. Penta Security Systems Co. has 18 years of background service in web security thanks to Penta Security Systems Inc. (KR), which has accumulated valuable experience while serving firms and institutions in the advanced and fiercely competitive APAC market.
Thanks to the trust earned from customers, Penta Security Systems Co. has grown very rapidly during 18 years in business, maintaining unmatched market shares in many areas of information security. Penta Security Systems Co.’s products include Cloudbric,[2] WAPPLES (a web application firewall; appliance and virtual versions available), D’Amo (a database encryption solution), ISSAC-Web and I-Sign Plus (PKI encryption products). Penta Security Systems Co. is the best vendor for web application firewall and database encryption products, and seeks to expand their presence globally with the mission of spreading “positive influence” by protecting information transmitted through computer technology.
Industry issues
With the rising popularity of the web, companies have gone online. Services including Internet banking and financial transactions, resident registration card issuances, as well as customer service platforms are all available as web services. These websites and mobile apps are all made of web apps.[3] As a result, application layer is often the pathway to companies' invaluable assets. Cyber criminals have shifted their attention accordingly, to the application layer, of which many security administrators still fail to secure. Most security solution enterprises are built around the network layer, not application layer. Over 70% of all vulnerabilities are at the web application layer.[4]
Web Application Firewall
A web application firewall (WAF) detects and blocks the attacks to a web site and prevents manipulation of web sites. In addition, it protects assets by preventing information leakage through web attacks.[5]

1st generation WAF
1st generation web application firewalls use a pattern matching solution with many false positives. It will assume your website is hacked when it did not actually happen. This error originates from having two simple lists. One list of IPs give access permission, and another list of IPs deny permission to access your website. Based on these lists alone, many firewall services inaccurately block innocent visitors who simply want to visit your website. It is extremely difficult to manage this generation of firewall products. It is also impossible to respond immediately to any new attacks that have not been discovered before. As a result, this generation of firewall products reduces the speed for web service.

2nd generation WAF
Although 2nd generation firewall is more accurate than the 1st, it has long a way to go. The way the 2nd generation firewall works is that it is exactly the same two lists as in the 1st generation, but automated. Even with this method, it takes a long time to analyze traffic prior to making these lists. Furthermore, every time you make changes to the website, it must go through another drawn out period of analysis to make those lists. Although 2nd generation firewall is automated, it still has to be managed by an administrator to make sure it is working properly. As this method is still based on pattern matching, it still can’t protect your website from prospective attacks because it doesn’t learn to predict new attacks.
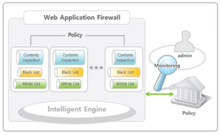
3rd generation WAF
In order to overcome the limitations of previous generations of firewalls, the Cloudbric team came up with an innovative method to make a 3rd generation prototype. Unlike previous generations, they use COCEP[6](Contents Classification and Evaluation Processing) instead of a pattern matching search paradigm which uses the method called signature-based security. In other words, Cloudbric is a 3rd generation firewall that uses a NON-SIGNATURE based product, and uses logical analysis rather than pattern matching. COCEP uses 26 different search parameters to do a detailed and accurate analysis on website traffic.
Product Features
Instead of using a signature-based pattern-matching method like that of other website protection services, Cloudbric has adopted the Logic Analysis Engine. This detection method is patented in South Korea, Japan, China (pending) and the U.S.(pending). Low false positive rate is what separates Cloudbric from other market players.
The official IT certification lab Tolly Group research institute rated WAPPLES considerably higher than a widely deployed competing product.[7] WAPPLES is the physical hardware geared with COCEP technology. The Tolly group's evaluation was based on effectiveness, performance and functionality of web application firewall.
OWASP Top 10 Protection
Cloudbric provides website shields from the ten most dangerous exploits, as identified annually by the Open Web Application Security Project (OWASP). The OWASP Top Ten represents a broad consensus about what the most critical web application security flaws are.[8]
Logic Analysis Engine
Cloudbric has adopted the patented Logic Analysis Engine, which understands the context of HTTP and its full transactions. By understanding these transactions, even if the attack scheme has no known signature-based patterns, Cloudbric can recognize malicious intent.[9] Cloudbric’s self-learning engine detects both known and unknown attacks with logical algorithms. It not only has a higher accuracy rate, but also doesn’t downgrade website performance.
PCI-Certified Web Application Firewall (WAF)
Cloudbric’s Web Application Firewall(WAF) is certified by the Payment Card Industry Security Standards Council. It delivers cost-effective compliance with Payment Card Industry Data Security Standard requirement 6.6 without any hardware or software installation and without changes to the user's web application. Cloudbric protects users from liabilities and non-compliance penalties, while protecting customers’ sensitive data from exposure on the site. The PCI compliance report audits security rules configuration changes and periodically reports on the user's compliance with PCI 6.6 requirements.[10]
References
- ↑ Glade, Jim (12 June 2015). "The Cloudbric effect". The Startup Mag. Retrieved 29 June 2015.
- ↑ "Penta Security Launches Cloudbric, the Cloud-Based WAF Service". Penta Security. Retrieved 2015-05-19.
- ↑ Penta Security, Penta Security. "he Core of Web Security = the Application Security". Penta Security. Penta Security. Retrieved 3 June 2015.
- ↑ Williams, Amrit. "Organizations Should Implement Web Application Security Scanning". Gartner. Gartner. Retrieved 3 June 2015.
- ↑ Penta Security, Penta Security. "Web Application Firewall (WAF)". Penta Security. Penta Security. Retrieved 3 June 2015.
- ↑ Penta Security Systems Inc., Penta Security Systems Inc. "Penta Security Receives IT Innovation Award from the Minister of Science, ICT and Future Planning". Penta Security Systems Inc. hwals.com.
- ↑ "Penta Security WAPPLES Web Application Firewall (WAF) Detection Effectiveness, Performance and Management Functionality Evaluation". Tolly. 2015-02-06. Retrieved 2015-05-19.
- ↑ owasp, owasp. "OWASP Top Ten Project". owasp.org. owasp.org. Retrieved 3 June 2015.
- ↑ Logic Engine Advantages, Web Application Security. "WAPPLES". SoftFarm. SoftFarm. Retrieved 3 June 2015.
- ↑ Information Supplement, PCI DSS. "Application reviews and web application firewalls clarified" (PDF). PCI. PCI Security Standards Council. Retrieved 3 June 2015.