Terrorist Tactics, Techniques, and Procedures
Terrorist Tactics, Techniques, and Procedures (TTPs) is an essential concept in terrorism studies.[1]
Role in terrorism analysis
The role of TTPs in terrorism analysis is that this concept is used to identify:
- Individual patterns of behavior of a particular terrorist activity, or a particular terrorist organisation.
- Examine and categorize more general tactics, and weapons used by a particular terrorist activity, or a particular terrorist organisation.
Requirement to identify individual terrorism TTPs
The current approach to terrorism analysis involves an examination of individual terrorist, or terrorist organisations use of particular weapons, used in specific ways, and different tactics and strategies being exhibited.[2] Broadly, a wide range of TTPs have been exhibited historically by individual terrorist, or terrorist organisations worldwide.[3]
Key TTP concepts
Evolution of terrorist TTPs
All terrorist, or terrorist organisations worldwide historically have exhibited an evolution in TTPs, these can be as a result:
- In response to changing circumstances;
- Resources availability; or,
- Changing ideologies, or 'war-focus'.
In the case of the Taliban, their tactics have consisted primarily of guerrilla-style improvised explosive device (IED) attacks and small-arms ambushes against international and state-level security forces and interests, such as police checkpoints and military supply convoys. However, more recently Taliban TTPs have expanded to include mass casualty attacks by suicide bombers and other suicide attacks in order to undermine the current government.
The Kill-Chain Model
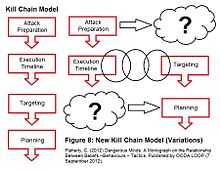
The 'Kill-Chain Model' (KCM) is a conceptual tool used in terrorism analysis, and studies.[4] All terrorist, or terrorist organisations' TTPs form part of understanding a terrorist's kill chain; which is the pattern of transactional activities, that are linked together in order for a terrorist act to take place. Broadly, this involves describing the 'hierarchy of tasks and sub-tasks that may be involved in the execution', or making happen a terrorist act.[5] These can involve,
- The arrangement and sequence of activities a terrorist, or terrorist organisations uses in planning, organizing, mobilizing, training, equipping and staging – resources and operatives.
- These activities make up the terrorist, or terrorist organisations' modus operandi, or what is known as 'its attack system.'[6]
Four sets of steps make-up the full KCM:
- The first set of activities identified in the KCM are the 'Attack Preparation Steps'. In terms of terrorism analysis, individual transactions, such as acquiring finances, acquiring expertise, acquiring materiel, munitions or capability, recruiting members, conducting reconnaissance, mission rehearsal, conducting an attack, etc. have signatures that identify them as terrorist or criminal acts or are consistent with the operations of a specific individual, cell or group.
- The second set of activities identified in the KCM are called the 'Execution Timeline'. This identifies the timeline, along which the terrorist, or terrorist organisations various activities, leading up to an attack process flows time-wise.
- The third set of activities identified in the KCM is identified as 'Targeting'. An individual or group would carry out some form of dedicated reconnaissance with the aim of identifying weaknesses in the site or operation; and with that information determine the best method of attack.
- The fourth set of activities identified in the KCM is identified as the 'Planning Stages'. These involve some type of planning activity embedded into the ‘kill-chain’, and is part of the process of organizing, mobilizing, training, equipping, staging, collecting resources and operatives. These make-up the terrorist, or terrorist organisations’ modus operandi, or its system of attack.
The KCM “sequence of activities”,[7] is not linear but is discontinuous. Three additional KCM scenarios can be identified:[8]
- An individual or group actively promote a terrorist/extremist ideology on the internet, in books, pamphlets, etc. This is then picked up by another terrorist, or terrorist organisations, who then act on this.
- Two or more parallel kill chain sequence of activities (by various individuals/groups) which are only indirectly connected by intermediary individuals/groups. Sharing similar beliefs, but as well cross over into complementary beliefs/ideologies. Many such intermediaries can operate in this space, passing ideas and resources, even recruits between the various terrorist, or terrorist organisations, groups and cells.
- A terrorist, or terrorist organisations picks up ideas, knowledge, etc., and jump-start into various places along the ‘standard’ concept of the KCM.
Transfer of Terrorist Tactics, Techniques and Procedures
Terrorist TTPs are often transferred between various terrorists, or terrorist organisations, and they often learn from each other.[9] The degree to which the transfer of TTPs occurs depends on their relative success when transferred to a different conflict, and a different environment. The similarities in TTPs between various terrorists, or terrorist organisations, across conflicts and periods suggest a transfer of information.
- Explicit Knowledge: This is the theoretical information which is often stored in hard copies, such as textbooks, manuals and on computers through PDF and video files. These are extremely easy to get hold of, but without the appropriate teaching or experience, this easy access information is commonly not effectively used.
- Tactical Knowledge: Most commonly taught or learnt through experience and hands on teaching. This requires training establishments to be organised. For terrorists, or terrorist organisations, acquiring this information is harder, and more difficult; however, it is seen as a more effective transfer of knowledge.
Key tactical concepts related to TTPs
Several key tactical concepts can be related to TTPs, which are typically used in terrorism or insurgency operations.
- Interposing tactics.[10]
- Mimicking operations.[11]
- Rhizome Manoeuvre.[12]
- Three-Dimensional (3D) Tactics Analysis.
- Swarming Tactics.
- Deliberate erratic actions, and erratic attacks;[13] and,
- Dynamic defence.[14]
References
- ↑ Sullivan, J.P. Bauer, A. (2008) Terrorism Early Warning: 10 Years of Achievement in Fighting Terrorism and Crime. Los Angeles, CA: Los Angeles Sheriff’s Department (December, 2008). URL: http://file.lacounty.gov/lasd/cms1_144939.pdf.
- ↑ http://file.lacounty.gov/lasd/cms1_144939.pdf
- ↑ Flaherty, C. (2012) Dangerous Minds: A Monograph on the Relationship Between Beliefs –Behaviours – Tactics. Published by OODA LOOP (7 September 2012).URL: http://www.oodaloop.com/security/2012/09/07/dangerous-minds-the-relationship-between-beliefs-behaviors-and-tactics/
- ↑ Sullivan, J.P. Bauer, A. (2008) Terrorism Early Warning: 10 Years of Achievement in Fighting Terrorism and Crime. Los Angeles, CA: Los Angeles Sheriff’s Department (December, 2008). URL: http://file.lacounty.gov/lasd/cms1_144939.pdf.
- ↑ http://file.lacounty.gov/lasd/cms1_144939.pdf
- ↑ http://file.lacounty.gov/lasd/cms1_144939.pdf
- ↑ Sullivan, J.P. Bauer, A. (2008) Terrorism Early Warning: 10 Years of Achievement in Fighting Terrorism and Crime. Los Angeles, CA: Los Angeles Sheriff’s Department (December, 2008). URL: http://file.lacounty.gov/lasd/cms1_144939.pdf.
- ↑ Flaherty, C. (2012) Dangerous Minds: A Monograph on the Relationship Between Beliefs –Behaviours – Tactics. Published by OODA LOOP (7 September 2012).URL: http://www.oodaloop.com/security/2012/09/07/dangerous-minds-the-relationship-between-beliefs-behaviors-and-tactics/
- ↑ Hedges, M. Karasik, T. Evolving Terrorist Tactics, Techniques, and Procedures (TTP) Migration Across South Asia, Caucasus, and the Middle East. INEGMA Special Report No. 7. URL: http://terror-mirror.com/books/etrrep014.pdf
- ↑ Flaherty, C. (2009) Interposing Tactics. Red Team Journal.com URL: http://redteamjournal.com/2009/12/interposing-tactics/
- ↑ Flaherty, C.J. (December 2003) Mimicking Operations, Australian Army Journal. (1)2: 11-14. URL: http://www.army.gov.au/Our-future/LWSC/Our-publications/Australian-Army-Journal/Past-issues/~/media/Files/Our%20future/LWSC%20Publications/AAJ/2003Summer/02-InformationWarfareAndMi.pdf
- ↑ Flaherty, C. (2012) Dangerous Minds: A Monograph on the Relationship Between Beliefs –Behaviours – Tactics. Published by OODA LOOP (7 September 2012).URL: http://www.oodaloop.com/security/2012/09/07/dangerous-minds-the-relationship-between-beliefs-behaviors-and-tactics/
- ↑ Flaherty, C. (2009) 2D Verses 3D Tactical Supremacy in Urban Operations. Journal of Information Warfare. (8)2: 13-24.
- ↑ Flaherty, C. (2009) 2D Verses 3D Tactical Supremacy in Urban Operations. Journal of Information Warfare. (8)2: 13-24.