Speck (cipher)
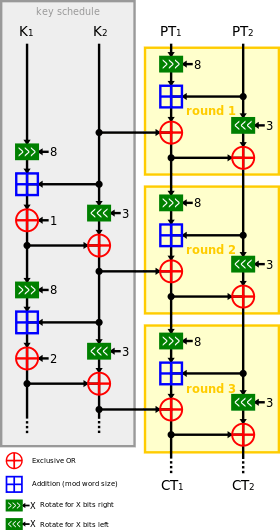 3 rounds of Speck with key schedule | |
| General | |
|---|---|
| Designers | Ray Beaulieu, Douglas Shors, Jason Smith, Stefan Treatman-Clark, Bryan Weeks, Louis Wingers NSA |
| First published | 2013 |
| Related to | Simon, Threefish |
| Cipher detail | |
| Key sizes | 64, 72, 96, 128, 144, 192 or 256 bits |
| Block sizes | 32, 48, 64, 96 or 128 bits |
| Structure | ARX |
| Rounds | 22, 23, 26, 27, 28, 29, 32, 33 or 34 (depending on block and key size) |
| Speed | 2.6 cpb (5.7 without SSE) on Intel Xeon 5640 (Speck128/128) |
| Best public cryptanalysis | |
| Differential cryptanalysis can break 17 rounds of Speck128/128 with 2113 data, 222 bytes memory and time complexity of 2113.[1] Rectangle attack can break 18 rounds of Speck128/192,256 with 2121.9 data, 2125.9 bytes memory and time complexity of 2182.7.[2] | |
Speck is a family of lightweight block ciphers publicly released by the NSA in June 2013.[3] Speck has been optimized for performance in software implementations, while its sister algorithm, Simon, has been optimized for hardware implementations. Speck is an add-rotate-xor (ARX) cipher.
Speck supports the following combinations of block sizes, key sizes and number of rounds:[4]
| Block size (bits) | Key size (bits) | Rounds |
|---|---|---|
| 32 | 64 | 22 |
| 48 | 72 | 22 |
| 96 | 23 | |
| 64 | 96 | 26 |
| 128 | 27 | |
| 96 | 96 | 28 |
| 144 | 29 | |
| 128 | 128 | 32 |
| 192 | 33 | |
| 256 | 34 |
Reference code
The following is the International Association for Cryptologic Research's ePrint reference implementation of the Speck variant with a 128-bit block size and key.[4]
#include <stdint.h> #define ROR(x, r) ((x >> r) | (x << (64 - r))) #define ROL(x, r) ((x << r) | (x >> (64 - r))) #define R(x, y, k) (x = ROR(x, 8), x += y, x ^= k, y = ROL(y, 3), y ^= x) void encrypt(uint64_t *pt, uint64_t *ct, uint64_t *K) { uint64_t i, B = K[1], A = K[0]; ct[0] = pt[0]; ct[1] = pt[1]; for(i = 0; i < 32; i++) { R(ct[1], ct[0], A); R(B, A, i); } }
References
- ↑ "Improved Differential Cryptanalysis of Round-Reduced Speck". Retrieved 2014-05-09.
- ↑ "Cryptanalysis of the Speck Family of Block Ciphers". Retrieved 2014-04-11.
- ↑ Schneier, Bruce. "Schneier on Security". Retrieved 2013-07-17.
- ↑ 4.0 4.1 "The Simon and Speck Families Of Lightwieght Block Ciphers". Retrieved 2014-01-29.