MaidSafe
 | |
| Original author(s) | David Irvine |
|---|---|
| Developer(s) | MaidSafe.net Limited |
| Development status | Active |
| Written in | C++ |
| Operating system | Microsoft Windows, OS X 10.4+, GNU/Linux (TBD) |
| Type | Decentralization |
| License | GNU GPLv3 (CLA required for contributions) and Proprietary option[1] |
| Alexa rank |
|
| Website |
maidsafe |
MaidSafe (Massive Array of Internet Disks - Secure Access For Everyone) is an open-source program (hosted on GitHub) that enables a decentralized internet platform. Instead of specialized servers, data is stored and distributed by a network of internet-connected computers. MaidSafe handles the allocation of hard disk space and communication between the computers (ensuring redundancy in case a computer goes offline). Data stored on the network is either encrypted or cryptographically signed by MaidSafe-connected applications (clients); the network itself cannot decrypt any of the data.
Users providing storage space to the network earn Safecoin, a digital currency that can be used to store information on the network.
History
David Irvine began work on MaidSafe in 2006. He raised $5 million for the project over the next year, eventually working with a team of 14 people.[3] The company is based in Troon, Scotland.[4]
In April 2014, MaidSafe used a crowdsale where it sold 400 million Safecoins[3] (10% of all Safecoins that can ever be produced, through another token call MaidSafeCoin[4]). It raised over $7 million in Mastercoins and Bitcoins. The value of the Mastercoins (half of the currency) subsequently declined, leaving the total from the sale at $5.5 million,[5][6] short of the hoped-for $8 million. The company is running test networks to prepare the software for an as-of-yet unscheduled official release.[4]
Mechanism
The MaidSafe system turns all connected devices into SAFE Network nodes that collectively store data for all MaidSafe users. MaidSafe allows public and private cloud data storage and processing within the SAFE Network. Data storage is automatically decentralized. This means a web application using MaidSafe does not store its user's data on any central server — rather the data is spread across many disks and devices owned and managed by many different users. No one person or corporation has an intact copy of a user's file.
Technical Details
Terminology
| Term | Meaning |
|---|---|
| Builder | A developer who creates applications for the SAFE Network in order to receive safecoin commissions. |
| MAID | Massive Array of Internet Disks |
| MaidSafe | The name of the project enabling the SAFE Network. |
| P.O.R. | Proof of Resource. A protocol used to measure a computer's resource contribution to the SAFE Network. |
| SAFE | Secure Access For Everyone |
| SAFE Network | A decentralized network of users, communicating through the distributed self-encryption technology created with MaidSafe. |
| Safecoin | A virtual currency that exists only on the SAFE Network. |
| User | Anyone who connects to the SAFE Network by running the MaidSafe program. |
| Vault | The allocated portion of a user's disk space, contributed to the SAFE Network. |
| Vault Farmer | A user who dedicates large amounts of storage space to the SAFE Network in order to farm safecoins. |
Clients
When a MaidSafe client joins the SAFE Network, the client agrees to give a portion of their device's local disk space or persistent memory space to the network. That space is called a vault. In return for supplying vault space, the client can store an equivalent amount of data to the network. A client can have many different devices connected to the MaidSafe network, each contributing some storage space to the network through its own vault. That client can then store an amount of data equivalent to the total space they've given to the network. For example, Bob connects both his personal laptop, a desktop computer and his tablet to MaidSafe. From his laptop he gives MaidSafe 100 MB, from his desktop he gives 350 MB and from his tablet his gives 8 MB. Since Bob has given a total of 458 MB to MaidSafe he now has access to 458 MB on the network which he can access from any device, anywhere and any time. In this way, the clients provide the network storage infrastructure.
Client Applications
MaidSafe client applications are the applications and services like cloud storage, encrypted messaging, web sites, virtual wallets, or document processing. Client applications providing these functions on the MaidSafe network do so using network features such as:
- Self Encrypting Data [7]
- Decentralized Public Key Infrastructure (providing network level Single Sign On move this note)
- Self Authentication [8]
(papers exist for each of these, they are on the wiki in github)
Client applications can access, store, mutate and communicate on the network. The clients allow people to anonymously join the network and cannot prevent people joining.
Data is presented to clients as virtual drives mounted on their machines, application data, internal to applications, communication data as well as dynamic data that is manipulated via client applications depending on the applications programmed methods.
Examples of client apps are cloud storage, encrypted messaging, web sites, crypto wallets, document processing of any data provided by any program, distributed databases, research sharing of documents, research and ideas with IPR protection if required, document signing, contract signing, decentralised co-operative groups or companies, trading mechanisms and many others. The clients can access every Internet service known today and introduce many services currently impossible.
Because authentication is done at the MaidSafe login, the SAFE network does not require any other passwords to access any further services. The client contains many cryptographically secured key pairs and can use these to automatically sign requests for session management or membership of any network service. Therefore a website with membership can present a join button and merely clicking that would sign an authority and allow access in the future. Digital voting, aggregated news, knowledge transfer of even very secret information is now all possible.
File storage
When a client stores a file on the SAFE network, the file is not stored intact on any single vault. Files are shredded into chunks and each chunk is encrypted. Multiple copies of the encrypted chunks are then scattered across the network, to many different vaults. When the client wants to retrieve a file, Maidsafe gathers all of the file's chunks, decrypts them and re-assembles them into the original document. So Bob's spreadsheet would be broken up and stored across vaults provided by Alice, Cameron and Dean. Neither Alice, Cameron or Dean would have a complete copy of Bob's spreadsheet stored in their vaults.
Vaults on devices like mobile phones and laptops may come and go from the SAFE network and cannot be relied upon to be connected 100% of the time. To accommodate for the transient connectedness of these devices, MaidSafe stores many copies of each chunk. Many copies of each file are stored on the SAFE network. Additionally, MaidSafe detects when the number of copies of a chunk has dropped below a minimum threshold and will create a new copy of that chunk. This action ensures that files are always available despite the network being inherently unreliable.
Data security
Data security on the SAFE Network is achieved through MaidSafe encryption and dispersion of data across the network.
Storage cost and credits
Provision of resources, mainly via storage of data shards produces a proof of resource token internal to the network. These tokens will be purchased by people for access when those people have either too little or no resources themselves.
Machines that store these data shards will be awarded safecoin by the network. This is very similar to Bitcoin mining, with the notable exception there is no waste. Each coin mined will have been the product of providing value to the network.
Safecoin is essentially an independent peer-to-peer payment system and digital currency and makes use of a distributed blockchain approach. This allows faster transactions, anonymity and privacy of any financial transaction on the SAFE Network. A safecoin transaction is a digitally signed message, transferring the ownership of safecoins from one safecoin address to another.
Claimed Innovations
MaidSafe says that the system offers the following:
Reliable UDP (rUDP)
Reliable UDP with encryption and managed connection capabilities (groups of connections using shared sockets, 10 connections per socket etc.)
Kademlia Routing Improvements
Improvements on Kademlia that include Public-key infrastructure and accurate network reconfiguration, due to reliable connections being the routing table nodes.
Data Vaults
Autonomous data handling network layer for secure structured data, unstructured data, communications etc.
Passport
A distributed PKI handling system with keychain management of asymmetric keys
Cross Platform Drive
Cross platform network aware virtual file system. Provides a filsystem API to the network for private, public and private shared information.
Self-Encrypted Data
File shredding and encryption library that operates in a sliding window of three chunks, allowing real time encryption and decryption of data via a filesystem API model (so write, read in any order at any point in the data).
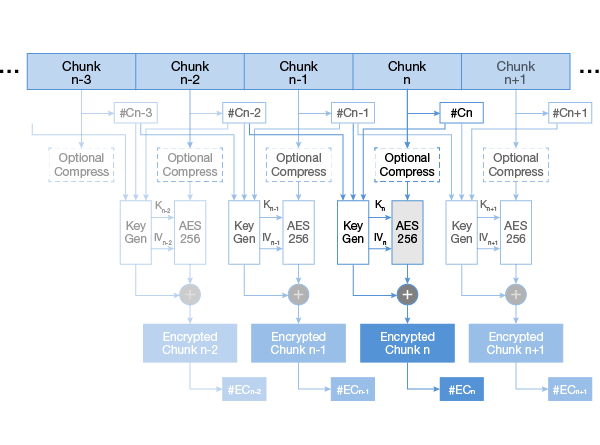
Applications
Device and OS Independent Data Access
An operating system built with MaidSafe may be able to allow its users to store large amounts of immediately available data and applications. This information would be available on almost every device in almost any location for that person, never again to lose data or blame a bad Operating System for losing important information. Operating system authentication would use a MaidSafe client to enable access. On successful login a virtual drive is mounted and the user has that mapped as their home drive, all data, settings, cache, etc., may be then immediately available.
Home NAS Providers
Installing a MaidSafe vault on home NAS devices could allow a family to share the space available. Due to the replication and de-duplication facets of the MaidSafe Platform it is likely that the disk may use space more efficiently. The family’s data can then be accessed from any location whether the house is powered on, broadband up or down or even when the device totally fails. Security concerns may also be alleviated using this method.
Search Providers
Search provision today is reliant on advertising as the income stream. This advertising is targeted for the maximum impact. Unfortunately this means significant intrusion into user privacy. This concern is increasingly becoming an issue in many sectors. Furthermore, the data processing required to serve targeted ads is significant, leading to large data centres and secured indexing mechanisms all behind corporate firewalls. Each data centre requires several years of costly advance planning for network provisioning (to address issues such as where will future customers be located, what demands will they put on hardware etc.) and will involve a large element of guesswork. The MaidSafe Platform is said to not allow search of data elements (chunks) and may actively see this as an attack and slow down a node attempting to search or perform a range based query. This is at the network level and above that level there is indexable data in many forms. Public data from public shares (as in today’s web) could be indexed as search engines do today (except on the MaidSafe network and not the web) so this component would be porting existing indexing algorithms across to the MaidSafe Platform. The MaidSafe Platform is claimed to not expose users data or credentials, and thus the intrusiveness of pattern matching targeted search provisioning becomes more acceptable. Using search algorithms, the MaidSafe client may be able to actively match users data with the MaidSafe Platform indexes and deliver targeted advertisements. Users may be able to switch off the ads should they become a nuisance or not relevant, to ensure user data is relatively accurate.
Data Storage / Sync Providers
Data storage systems face many issues; decreasing hard disk costs, reducing broadband prices (a double edged sword) and concerns over lack of security. Arguably there is some level of encryption in such systems, although this is hotly disputed as to its effectiveness. Many of the systems face cross platform or performance issues and may require to expand the offering beyond synchronised or server stored data sets. The MaidSafe Platform could possibly allow these companies to replace their existing technology with a scalable system that has extendibility at its heart. Security or privacy issues as well as speed, cross platform concerns or lack of services may be improved. The ability to extend offerings beyond a single OS, or service such as file availability to MaidSafe, may yield a monetary and competitive advantage. MaidSafe is said to require no data centre, each user brings their own resources and those resources appear where the users are (ready provisioned networking). This means data storage costs could potentially be significantly reduced and with it the potential for competing with suppliers. OS access screens could use a MaidSafe client to allow access. On successful login a virtual drive is mounted and the user has that mapped as their home drive, all data, settings, cache etc., is then available. In addition, communications, applications and a host of additional services could be made available.
Video Providers
Currently video serving via a web interface works well, recently further inroads have been made to encourage users to sign in for greater service. This is a service where costs are high, servers require significant upgrading and administration and bandwidth provisioning is non trivial. Using the MaidSafe Platform to allow users to store their own videos to the network and signposting these videos (as these companies do already) could potentially reduce costs associated with the back end systems currently employed. This could also ensure no DDOS attacks or server outages would occur (there are no servers). Login would be via a MaidSafe client key (requiring no interaction from the user) to recognise an entity on the network. No password lists, no user lists are required. A company installs a MaidSafe client and vault (as any person using MaidSafe would) and makes space available publicly, this space may allow users to 'upload' video to the site to be shared with others. The site itself may require additional work to allow the unstructured data type required from uploading videos.
Big Data Analysis Providers
Big data handling is a relatively new area of IT. Current systems such as Hadoop networks scale reasonably well to circa 4,500 nodes and in many cases depend on local fire-walled high speed networks with single failure points (name server), others require significant administration setup and monitoring. Most, if not all, of these systems cannot run in public networks as they are not secured and do not carry secure data. The MaidSafe platform may be able to allow planet wide networking that can handle a large amount of data on a public network, providing structured data handling, allowing index creation and querying. As with existing systems many query 'engines' could potentially be created and coded specifically for the problem being solved.
Virtual Currency Providers
Virtual currency has a wallet security issue, storing wallets on third party servers is neither secure or safe. Many such systems allow local wallets to be created and secured by encrypting the disk on file. This is slightly safer than no encryption but does not prevent corruption or theft in many cases, it also provides issues with synchronising the wallet between devices as again this would require a trusted third party. Using the MaidSafe Platform this wallet could possibly be available on every device in any location for that person and only that person: existing clients such as the Bitcoin wallets have to locate the wallet to the virtual drive users have available after logging into the MaidSafe network.
Single Sign On Systems
Users have to remember so many passwords that the quantity and quality of them may significantly reduce security (users often choose the same password for many systems). Single sign-on systems attempt to overcome this, but they may require trust between providers, and in some cases they expose users to privacy intrusion. A MaidSafe client may have the ability to create multiple cryptographic ID's including public ID's. These public ID's can range from fully qualified (validate age, address etc.) to anonymous ones. Even anonymous ID's would validate repeatedly, potentially guaranteeing the entity logging in is consistently validated to be the same. The app or site being accessed only has to confirm the user by checking a cryptographic signature. Users may be able to login to services without a username or password, meaning entities that supply services may be able to do so securely and never store any user passwords, etc., potentially becoming more resistant to break-ins.
Sites in this case have to supply an access page that validates users automatically. The MaidSafe client requires an API method to accomplish this.
See also
- Freenet - similar project
- GNUnet
- I2P
- Osiris sps
- Java Anon Proxy (also known as JonDonym)
- Tor (internet browsing anonymity)
- Tor hidden service (anonymity of both browsing and publishing)
- The Hidden Wiki (censorship-resistant wiki that anyone can anonymously edit)
- Share - the successor to Winny
- Perfect Dark - the successor to Share; it employs many of Freenet's principles.
- Tahoe-LAFS
- Entropy (anonymous data store) (Discontinued)
References
- ↑ "MaidSafe Commercial License". MaidSafe.net Limited.
- ↑ "MaidSafe.net Site Info". Alexa Internet. Retrieved 2014-06-28.
- ↑ 3.0 3.1 Hill, Kashmir (8 April 2014). "Beyond Bitcoin: Crypto-Ownership Companies Hope You're Ready To Decentralize Everything On The Internet". Forbes. Retrieved 30 July 2014.
- ↑ 4.0 4.1 4.2 Bradbury, Danny (25 June 2014). "MaidSafe COO Reflects on Lessons Learned from Crowdsale". CoinDesk. Retrieved 30 July 2014.
- ↑ Bradbury, Danny (25 June 2014). "MaidSafe COO Reflects on Lessons Learned from Crowdsale". CoinDesk. Retrieved 28 July 2014.
- ↑ Hill, Kashmir (3 June 2014). "The First 'Bitcoin 2.0' Crowd Sale Was A Wildly Successful $7 Million Disaster". Forbes. Retrieved 28 July 2014.
- ↑ "Self Encryption Process Patent".
- ↑ "Self Authentication Paper" (PDF). MaidSafe.net Limited.