Equation Group
The Equation Group is a highly advanced secretive computer espionage group, suspected by security expert Claudio Guarnieri[1] and unnamed former intelligence operatives[2] of being tied to the United States National Security Agency (NSA). Because of the group's predilection for strong encryption methods in their operations, the name Equation Group was chosen by Kaspersky Lab, which discovered this operation and also documented 500 malware infections by the group's tools in at least 42 countries.[3][4]
Summary
At the Kaspersky Security Analysts Summit held in Mexico on February 16, 2015, Kaspersky Lab announced its discovery of the Equation Group. According to Kaspersky Lab's report, the group has been active since at least 2001, with more than 60 actors.[5] The malware used in their operations, dubbed EquationDrug and GrayFish, is found to be capable of reprogramming hard disk drive firmware.[6] Because of the advanced techniques involved and high degree of covertness, the group is suspected of ties to the NSA, but Kaspersky Lab has not identified the actors behind the group.
The NSA codewords "BACKSNARF", "Grok", "STRAITACID," and "STRAITSHOOTER" have all been found inside the malware. In addition, timestamps in the malware seem to indicate that the programmers worked overwhelmingly Monday-Friday in what would correspond to a 08:00-17:00 workday in an Eastern United States timezone.[7]
IRATEMONK and Equation Group
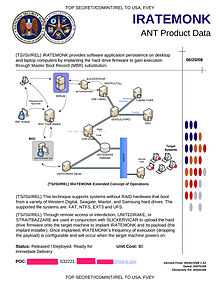
F-Secure claims that the Equation Group's malicious hard drive firmware is the Tailored Access Operations program "IRATEMONK" that is listed in the NSA ANT catalog.[8] IRATEMONK provides the attacker with an ability to have their software application persistently installed on desktop and laptop computers, despite the disk being formatted, its data erased or the operating system re-installed. It infects the hard drive firmware, which in turn adds instructions to the disk's master boot record that causes the software to install each time the computer is booted up.[9] It is capable of infecting certain hard drives from Seagate, Maxtor, Western Digital, Samsung,[9] IBM, Micron and Toshiba.[6]
The text of IRATEMONK's listing in the NSA ANT catalog:[9]
(TS//SI//REL) IRATEMONK provides software application persistence on desktop and laptop computers by implanting in the hard drive firmware to gain execution through Master Boot Record (MBR) substitution.(TS//SI//REL) This technique supports systems without RAID hardware that boot from a variety of Western Digital, Seagate, Maxtor, and Samsung hard drives. The supported file systems are: FAT, NTFS, EXT3 and UFS.
(TS//SI//REL) Through remote access or interdiction, UNITEDRAKE, or STRAITBAZZARE are used with SLICKERVICAR to upload the hard drive firmware onto the target machine to implant IRATEMONK and its payload (the implant installer). Once implanted, IRATEMONK's frequency of execution (dropping the payload) is configurable and will occur when the target machine powers on.
Status: Released / Deployed. Ready for Immediate Delivery
Unit Cost: $0
Fanny.bmp
Kaspersky's global research and analysis team, otherwise known as GReAT, claimed to have found a piece of malware that contained Stuxnet's "privLib" in 2008.[10] Specifically it contained the LNK exploit found Stuxnet in 2010. Fanny is classified as a worm that affects certain windows operating systems and attempts to spread laterally via network connection or usb storage. Kaspersky stated that they suspect that because of the recorded compile time of Fanny that the Equation Group has been around longer than Stuxnet.[11]
See also
- Global surveillance disclosures (2013–present)
- United States intelligence operations abroad
- NSA's Hard Drive Firmware Hack
References
- ↑ "Equation = NSA? Researchers Uncloak Huge 'American Cyber Arsenal'". Forbes.
- ↑ "Russian researchers expose breakthrough U.S. spying program". Reuters.
- ↑ "How "omnipotent" hackers tied to NSA hid for 14 years—and were found at last". Ars Technica.
- ↑ Jeremy Kirk (17 February 2015). "Destroying your hard drive is the only way to stop this super-advanced malware". PCWorld.
- ↑ "Equation Group: The Crown Creator of Cyber-Espionage". Kaspersky Lab.
- ↑ 6.0 6.1 "Equation: The Death Star of Malware Galaxy". Kaspersky Lab.
- ↑ "New smoking gun further ties NSA to omnipotent "Equation Group" hackers". Ars Technica.
- ↑ "The Equation Group Equals NSA / IRATEMONK - F-Secure Weblog : News from the Lab".
- ↑ 9.0 9.1 9.2 "IRATEMONK: NSA Exploit of the Day". Schneier on Security.
- ↑ (source)
- ↑
External links
| Wikimedia Commons has media related to Equation Group. |
- Equation Group: Questions and Answers by Kaspersky Lab, Version: 1.5, February 2015
- A Fanny Equation: "I am your father, Stuxnet" by Kaspersky Lab, February 2015