Blom's scheme
Blom's scheme is a symmetric threshold key exchange protocol in cryptography. The scheme was proposed by the Swedish cryptographer Rolf Blom in a series of articles in the early 1980s.[1][2]
A trusted party gives each participant a secret key and a public identifier, which enables any two participants to independently create a shared key for communicating. However, if an attacker can compromise the keys of at least k users, he can break the scheme and reconstruct every shared key. Blom's scheme is a form of threshold secret sharing.
Blom's scheme is currently used by the HDCP copy protection scheme to generate shared keys for high-definition content sources and receivers, such as HD DVD players and high-definition televisions.
The protocol
The key exchange protocol involves a trusted party (Trent) and a group of  users. Let Alice and Bob be two users of the group.
users. Let Alice and Bob be two users of the group.
Protocol setup
Trent chooses a random and secret symmetric matrix 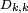 over the finite field
over the finite field 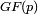 , where p is a prime number.
, where p is a prime number. 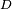 is required when a new user is to be added to the key sharing group.
is required when a new user is to be added to the key sharing group.
For example:
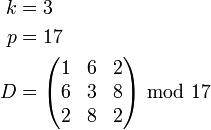
Inserting a new participant
New users Alice and Bob want to join the key exchanging group. Trent chooses public identifiers for each of them; i.e., k-element vectors:
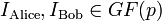 .
.
For example:
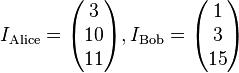
Trent then computes their private keys:
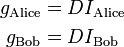
Using 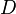 as described above:
as described above:
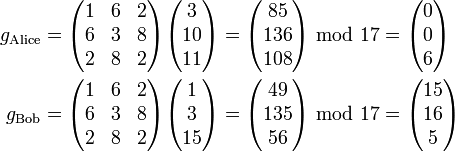
Each will use their private key to compute shared keys with other participants of the group.
Computing a shared key between Alice and Bob
Now Alice and Bob wish to communicate with one another. Alice has Bob's identifier 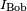 and her private key
and her private key 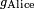 .
.
She computes the shared key 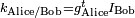 , where
, where  denotes matrix transpose. Bob does the same, using his private key and her identifier, giving the same result:
denotes matrix transpose. Bob does the same, using his private key and her identifier, giving the same result:
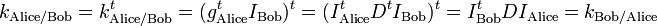
They will each generate their shared key as follows:
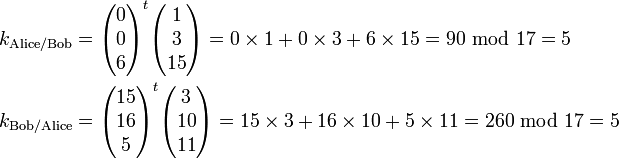
Attack resistance
In order to ensure at least k keys must be compromised before every shared key can be computed by an attacker, identifiers must be k-linearly independent: all sets of k randomly selected user identifiers must be linearly independent. Otherwise, a group of malicious users can compute the key of any other member whose identifier is linearly dependent to theirs. To ensure this property, the identifiers shall be preferably chosen from a MDS-Code matrix (maximum distance separable error correction code matrix). The rows of the MDS-Matrix would be the identifiers of the users. A MDS-Code matrix can be chosen in practice using the code-matrix of the Reed–Solomon error correction code (this error correction code requires only easily understandable mathematics and can be computed extremely quickly).[3]
References
- ↑ Blom, Rolf. Non-public key distribution. In Proc. CRYPTO 82, pages 231–236, New York, 1983. Plenum Press
- ↑ Blom, Rolf. "An optimal class of symmetric key generation systems", Report LiTH-ISY-I-0641, Linköping University, 1984
- ↑ Menezes, A, Paul C. van Oorschot and Scott A. Vanstone (1996). Handbook of Applied Cryptography. CRC Press. ISBN 0-8493-8523-7.