Subliminal channel
In cryptography, subliminal channels are covert channels that can be used to communicate secretly in normal looking communication over an insecure channel.[1] Subliminal channels in digital signature crypto systems were found in 1984 by Gustavus Simmons.
Simmons describes how the dilemma can be solved through parameter substitution in digital signature algorithms.[2] Signature algorithms like ElGamal and DSA have parameters which must be set with random information. He shows how one can make use of these parameters to send a message subliminally. Because the algorithm's signature creation procedure is unchanged, the signature remains verifiable and indistinguishable from a normal signature. Therefore it is hard to detect if the subliminal channel is used.
Subliminal channels can be classified into broadband and narrow-band channel. The broadband channel uses almost all available bits. Every channel which uses fewer bits is called a narrow-band channel. The additional used bits are needed for further protection, e.g., impersonation.The broadband and the narrow-band channels can use different algorithm parameters. A narrow-band channel cannot transport maximal information, but it preserves the authentication key. Further developments enhance the subliminal channel, e.g., allow for establishing a broadband channel without the need to agree on an authentication key in advance. Other developments try to avoid the entire subliminal channel.
Examples
An easy example of a narrowband subliminal channel for normal human-language text would be to define that an even word count in a sentence is associated with the bit "0" and an odd word count with the bit "1". The question "Hello, how do you do?" would therefore send the subliminal message "1".
The Digital Signature Algorithm has one subliminal broadband[3] and three subliminal narrow-band channels [4]
At signing the parameter  has to be set random. For the broadband channel this parameter is instead set with a subliminal message
has to be set random. For the broadband channel this parameter is instead set with a subliminal message  .
.
- Key generation
- choose prime

- choose prime

- calculate generator

- choose authentication key
 and send it securely to the receiver
and send it securely to the receiver - calculate public key
 mod
mod 
- choose prime
- Signing
- choose message
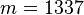
- (hash function
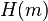 is here substituted with a modulo reduction by 107) calculate message hash value
is here substituted with a modulo reduction by 107) calculate message hash value  mod
mod  mod
mod 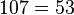
- instead of random value
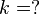 subliminal message
subliminal message  is chosen
is chosen - calculate inverse of the subliminal message
 mod
mod 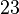
- calculate signature value
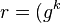 mod
mod 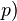 mod
mod 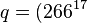 mod
mod 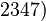 mod
mod 
- calculate signature value
 mod
mod  mod
mod 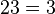
- sending message with signature triple
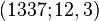
- choose message
- Verifying
- receiver gets message triple
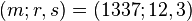
- calculate message hash
 mod
mod  mod
mod 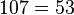
- calculate inverse
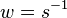 mod
mod 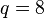
- calculate
 mod
mod 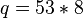 mod
mod 
- calculate
 mod
mod  mod
mod 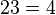
- calculate signature
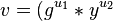 mod
mod 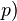 mod
mod 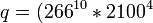 mod
mod 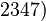 mod
mod 
- since
 , the is signature valid
, the is signature valid
- receiver gets message triple
- Message extraction on receiver side
- from triple (1337; 12, 3)
- extract message
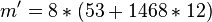 mod
mod 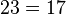
The formula for message extraction is derived by transposing the signature value  calculation formula.
calculation formula.
-
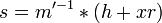 mod
mod 
-
 mod
mod 
-
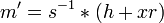 mod
mod 
Example - RSA Case study
Here is a (real, working) PGP public key (using the RSA algorithm), which was generated to include two subliminal channels - the first is the "key ID", which should normally be random hex, but below is "covertly" modified to read "C0DED00D". The second is the base64 representation of the public key - again, supposed to be all random gibberish, but the English-readable message "//This+is+Christopher+Drakes+PGP+public+key//Who/What+is+watcHIng+you//" has been inserted. Adding both these subliminal messages was accomplished by tampering with the random number generation during the RSA key generation phase.
PGP Key. RSA 2020/C0DED00D Fprint: 250A 7E38 9A1F 8A86 0811 C704 AF21 222C
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: Private
mQESAgAAAAAAAAEH5Ar//This+is+Christopher+Drakes+PGP+public+key//
Who/What+is+watcHIng+you//Di0nAraP+Ebz+iq83gCa06rGL4+hc9Gdsq667x
8FrpohTQzOlMF1Mj6aHeH2iy7+OcN7lL0tCJuvVGZ5lQxVAjhX8Lc98XjLm3vr1w
ZBa9slDAvv98rJ8+8YGQQPJsQKq3L3rN9kabusMs0ZMuJQdOX3eBRdmurtGlQ6AQ
AfjzUm8z5/2w0sYLc2g+aIlRkedDJWAFeJwAVENaY0LfkD3qpPFIhALN5MEWzdHt
Apc0WrnjJDby5oPz1DXxg6jaHD/WD8De0A0ARRAAAAAAAAAAAbQvQ2hyaXN0b3Bo
ZXIgRHJha2UgPENocmlzdG9waGVyLkRyYWtlQFBvQm94LmNvbT60SE5ldFNhZmUg
c2VjdXJpdHkgc29mdHdhcmUgZGlyZWN0b3IgQ2hyaXN0b3BoZXIgRHJha2UgPE5l
dFNhZmVAUG9Cb3guY29tPokBEgMFEDPXgvkcP9YPwN7QDQEB25oH4wWEhg9cBshB
i6l17fJRqIJpXKAz4Zt0CfAfXphRGXC7wC9bCYzpHZSerOi1pd3TpHWyGX3HjGEP
6hyPfMldN/sm5MzOqgFc2pO5Ke5ukfgxI05NI0+OKrfc5NQnDOBHcm47EkK9TsnM
c3Gz7HlWcHL6llRFwk75TWwSTVbfURbXKx4sC+nNExW7oJRKqpuN0JZxQxZaELdg
9wtdArqW/SY7jXQn//YJV/kftKvFrA24UYLxvGOXfZXpP7Gl2CGkDI6fzism75ya
xSAgn9B7BqQ4BLY5Vn+viS++6Rdavykyd8j9sDAK+oPz/qRtYJrMvTqBErN4C5uA
IV88P1U=
=/BRt
-----END PGP PUBLIC KEY BLOCK-----
Improvements
A modification to the Brickell and DeLaurentis signature scheme provides a broadband channel without the necessity to share the authentication key.[5] The Newton channel is not a subliminal channel, but it can be viewed as an enhancement.[6]
Countermeasures
With the help of the zero-knowledge proof and the commitment scheme it is possible to prevent the usage of the subliminal channel.[7] It should be mentioned that the countermeasure from [7] has a 1-bit subliminal channel. The reason for that is the problem that a proof can succeed or purposely fail.[8]
Another countermeasure can detect, but not prevent, the subliminal usage of the randomness.[9]
References
- ↑ Gustavus J. Simmons. The Prisoners Problem and the Subliminal Channel. In Advances in Cryptology – CRYPTO ’83, pages 51–67, New York, 1984. Lecture Notes in Computer Science, ed. D. Chaum.
- ↑ Gustavus J. Simmons. The subliminal channel and digital signatures. In Proc. of the EUROCRYPT 84 workshop on Advances in cryptology: theory and application of cryptographic techniques, pages 364–378, New York, NY, USA, 1985. Springer-Verlag New York, Inc.
- ↑ Gustavus J. Simmons. Subliminal communication is easy using the DSA. In EUROCRYPT ’93: Workshop on the theory and application of cryptographic techniques on Advances in cryptology, pages 218–232, Secaucus, NJ, USA, 1994. Springer-Verlag New York, Inc.
- ↑ Gustavus J. Simmons. The subliminal channel in the U.S. Digital Signature Algorithm (DSA), in Proceedings of the 3rd Symposium on State and Progress of Research in Cryptography (SPRC '93), Rome, Italy, February 15–16, 1993.
- ↑ Gustavus J. Simmons. A Secure Subliminal Channel (?). In CRYPTO ’85: Advances in Cryptology, pages 33–41, London, UK, 1986. Springer-Verlag.
- ↑ Ross J. Anderson, Serge Vaudenay, Bart Preneel, and Kaisa Nyberg. The Newton Channel. In Proceedings of the First International Workshop on Information Hiding, pages 151–156, London, UK, 1996. Springer-Verlag.
- ↑ 7.0 7.1 Yvo Desmedt. Abuses in Cryptography and How to Fight Them. In CRYPTO ’88: Proceedings of the 8th Annual International Cryptology Conference on Advances in Cryptology, pages 375–389, London, UK, 1990. Springer-Verlag.
- ↑ Desmedt, Yvo (1996). "Simmons’ Protocol is Not Free of Subliminal Channels". Proc. of 9th IEEE Computer Security Foundations Workshop. pp. 170–175. CiteSeerX: 10.1.1.56.4816.
- ↑ Choi, Jong Youl; Golle, Philippe; Jakobsson, Markus (2006). "Tamper Evident Digital Signatures: Protecting Certification Authorities Against Malware". Proceedings of the 2nd IEEE International Symposium on Dependable Autonomic and Secure Computing. CiteSeerX: 10.1.1.61.9340.
- Bruce Schneier. Applied Cryptography, Second Edition: Protocols, Algorithms, and Source Code in C, 2. Ed. Wiley Computer Publishing, John Wiley & Sons, Inc., 1995.