Proactive secret sharing
Proactive secret sharing is a method to update distributed keys (shares) in a secret sharing scheme periodically such that an attacker has less time to compromise shares. This contrasts to a non-proactive scheme where if the threshold number of shares are compromised during the lifetime of the secret, the secret is compromised.
Motivation
If the players (holders of the shared secret) store their shares on insecure computer servers, an attacker could crack in and steal the shares. Since it is not often practical to change the secret, the uncompromised (Shamir-style) shares should be updated in a way that they generate the same secret, yet the old shares are invalidated.
Mathematics
In order to update the shares, the dealer (i.e., the person who gives out the shares) generates a new random polynomial with constant term zero and calculates for each remaining player a new ordered pair, where the x-coordinates of the old and new pairs are the same. Each player then adds the old and new y-coordinates to each other and keeps the result as the new y-coordinate of the secret.
- The dealer constructs a random polynomial over a field of degree
 where
where  is the threshold
is the threshold - Each player gets the share
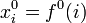 where
where  ,
,  is the number of players, and
is the number of players, and  is the share for player
is the share for player  at time interval
at time interval 
- The secret can be reconstructed via interpolation of
 shares
shares - To update the shares, all parties need to construct a random polynomial of the form

- Each player
 sends all other players
sends all other players 
- Each player updates their share by
 where
where 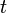 is the time interval in which the shares are valid
is the time interval in which the shares are valid
All of the non-updated shares the attacker accumulated become useless. An attacker can only recover the secret if he can find enough other non-updated shares to reach the threshold. This situation should not happen because the players deleted their old shares. Additionally, an attacker cannot recover any information about the original secret from the update process because it only contains random information.
The dealer can change the threshold number while distributing updates, but must always remain vigilant of players keeping expired shares.
Example
The following example has 2 shares and a threshold of 2 with 2 players and 1 dealer. Since shares and polynomials are only valid for a certain time period, the time period they are valid is denoted with a superscript.
- All parties agree on a finite field:

- The dealer establishes a secret:
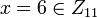
- The dealer constructs a random polynomial over
 of degree 2 - 1 (threshold of 2)
of degree 2 - 1 (threshold of 2)
-
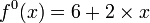
- note

-
- Player 1 gets share
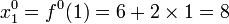 and player 2 gets share
and player 2 gets share 
- To reconstruct the secret, use
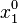 and
and 
- Since
 is a line, we can use point slope form to interpolate
is a line, we can use point slope form to interpolate -

-

-

-

- Since
- To update the shares, all parties need to construct random polynomials of degree 1 such that the free coefficient is zero
- Player 1 constructs
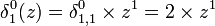
- Player 2 constructs
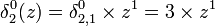
- Player 1 constructs
- Each player evaluates their polynomial and shares some information with other players
- Player 1 computes
 and
and  in
in 
- Player 1 sends Player 2

- Player 2 computes
 and
and  in
in 
- Player 2 sends Player 1

- Player 1 computes
- Each player updates their share by

- Player 1 computes

- Player 2 computes

- Player 1 computes
- Confirm updated shares generate same original secret
- Use
 and
and 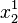 to reconstruct the polynomial
to reconstruct the polynomial 
- Since
 is a line, we can use point slope
is a line, we can use point slope -

-

-

-

- Use
See also
References
- Herzberg, Amir; Jarecki, Stanislaw; Hugo, Krawczyk; Yung, Moti (1995). "Proactive Secret Sharing Or: How to Cope With Perpetual Leakage". CRYPTO '95: Proceedings of the 15th Annual International Cryptology Conference on Advances in Cryptology (London, UK: Springer-Verlag): 339–352. ISBN 3-540-60221-6. Retrieved June 14, 2010.
- Yevdokimov, Aleksey (2009). "Dynamic system of proactive security". Application of Information and Communication Technologies, 2009. AICT 2009. (Baku, Azerbaijan: IEEE): 1–4. ISBN 978-1-4244-4739-8. Retrieved June 14, 2010.
| ||||||||||