Bitcoin protocol
The Bitcoin protocol for the Bitcoin cryptocurrency is an open source cryptographic protocol that operates on a peer-to-peer network. It uses a chain or "block chain" of transactions to achieve consensus and to solve the double-spending problem. The block chain is distributed internationally using peer-to-peer filesharing technology similar to BitTorrent. It was designed in 2008 and released in 2009 by "Satoshi Nakamoto", the pseudonym of the original developer or group of developers.
The network timestamps transactions by including them in blocks that form an ongoing chain called the block chain. Such blocks cannot be changed without redoing the work that was required to create each block since the modified block. The longest chain serves not only as proof of the sequence of events but also records that this sequence of events was verified by a majority of the Bitcoin network's computing power. As long as a majority of computing power is controlled by nodes that are not cooperating to attack the network, they will generate the longest chain of records and outpace attackers.
The network itself requires minimal structure to share transactions. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will. Upon reconnection, a node will download and verify new blocks from other nodes to complete its local copy of the block chain.[1][2]
Bitcoins
A bitcoin is a currency object — an entity which is traded, though nothing prevents trades in fractions of, or multiple bitcoins. All bitcoins are intended to be equivalent, though they each have a separate, distinct history. A transaction creates and destroys (invalidates) bitcoins, creating the same amount as it destroys.
A bitcoin is defined by a chain of digitally signed transactions that began with its creation as a block reward. The owner of a bitcoin transfers it to the next owner by digitally signing it over to the next owner in a Bitcoin transaction, much like endorsing a traditional bank check. A payee can verify each previous transaction to verify the chain of ownership.
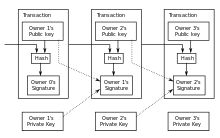
Although it would be possible to handle bitcoins individually, it would be unwieldy to make a separate transaction for every satoshi in a transfer. Transactions are therefore allowed to contain multiple inputs and outputs, and in that way bitcoins can be split and combined. Common transactions will have either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender. Any difference between the total input and output amounts of a transaction is offered to miners as a transaction fee.
It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here. Since the network verifies every transaction along the way, there is never the need to extract a complete standalone copy of a transaction's history.
Hashes and signatures
Two consecutive SHA-256 hashes are used for transaction verification. RIPEMD-160 is used after a SHA-256 hash for Bitcoin digital signatures or "addresses". A Bitcoin address is the hash of an ECDSA public-key, computed as follows:
Key hash = Version concatenated with RIPEMD-160(SHA-256(public key)) Checksum = 1st 4 bytes of SHA-256(SHA-256(Key hash)) Bitcoin address = Base58Encode(Key hash concatenated with Checksum)
Bitcoin addresses

Bitcoin addresses are randomly generated cryptographic public key pairs. Each public address consists of around 33 numbers and letters, beginning with the digit 1 or 3, as in the example of 1FfmbHfnpaZjKFvyi1okTjJJusN455paPH.[3]
The ability to transact bitcoins without the assistance of a central registry is facilitated in part by the availability of a virtually unlimited supply of unique addresses which can be generated and disposed of at will. A Bitcoin address has three fundamental properties:
- A Bitcoin balance - which is a matter of public record. This balance can be ascertained by looking up the transactions to and from any public address in the world-wide register of all Bitcoin transactions, called the "block chain".
- A public address - which may be shared with anyone and is used to specify a recipient when sending bitcoins.
- A private key - which is kept secret by the owner of the address. All valid transfers of bitcoins are digitally signed using the private key associated with the address sending the bitcoins.
Bitcoin wallets
Bitcoin users manage their Bitcoin addresses by using a digital wallet. Wallets let users send bitcoins, request payment, calculate the total balance of addresses in use, and generate new addresses as needed. Many wallets include precautions to keep the private keys secret, for example by encrypting the wallet data with a password or by requiring two-factor authenticated logins.
Bitcoin wallets have been implemented as stand-alone software applications, web applications, and even printed documents or memorized passphrases.
Software wallets
Software that directly connects to the peer-to-peer Bitcoin network includes bitcoind and Bitcoin-Qt, the bitcoind GUI counterpart available for Linux, Windows, and Mac OS X. Other less resource intensive Bitcoin wallets have been developed, including mobile apps for iOS and Android devices that display and scan QR codes to simplify transactions between buyers and sellers.[4] Theoretically, the services typically provided by an application on a general purpose computer could be built into a stand-alone hardware device, and several projects aim to bring such a device to market.[5]
Website wallets
Many Bitcoin websites provide addresses associated with an online account to hold Bitcoin funds on the user's behalf. Some of these sites work like bank accounts for Bitcoin, even paying interest. Other sites function primarily as real-time markets, facilitating the sale and purchase of bitcoins with other currencies such as US Dollars or Euros.

Paper wallets
Any valid Bitcoin address keys may be printed on paper and used to store bitcoins offline. Compared with "hot wallets"—those that are connected to the Internet—these non-digital offline paper wallets are considered a "cold storage" mechanism better suited for safekeeping bitcoins.[6] It is safe to use only if you have printed the paper yourself. Every such "cold storage" paper obtained from a second party as a present, gift, or payment should be immediately transferred to the safer wallet because the private key could have been copied and preserved by a grantor.
Various vendors offer banknotes, coins and cards denominated in bitcoins.[7] Bitcoin balance is bound to the private key printed on the banknote or embedded within the coin. Some of these instruments employ a tamper-evident seal that hides the private key. It is generally an insecure "cold storage" because one can't be sure that the producer of a banknote or a coin had destroyed the private key after the end of a printing process and doesn't preserve it. Tamper-evident seal in this case doesn't provide the needed level of security because the private key could be copied before the seal was applied on a coin. Some vendors will allow the user to verify the balance of a physical coin on their website, however that requires trusting that the vendor did not store the private key and is not showing a fabricated balance.
Timestamps
The Bitcoin specification starts with the concept of a distributed timestamp server. A timestamp server works by taking a SHA256 hash function of some data and widely publishing the hash, for instance, in a newspaper or Usenet post. The timestamp proves that the data must have existed at the time, in order to produce the hash. For Bitcoin, each timestamp includes the previous timestamp hash as input for its own hash. This dependency of one hash on another is what forms a chain, with each additional timestamp providing evidence that each of the previous timestamp hashes existed.
Bitcoin mining
To form a distributed timestamp server as a peer-to-peer network, Bitcoin uses a proof-of-work system similar to Adam Back's Hashcash and the internet rather than newspaper or Usenet posts.[2] The work in this system is what is often referred to as Bitcoin mining.
The mining process involves scanning for a value that when hashed twice with SHA-256, begins with a number of zero bits. While the average work required increases exponentially with the number of leading zero bits required, a hash can always be verified by executing a single round of double SHA-256.
For the Bitcoin timestamp network, a valid "proof-of-work" is found by incrementing a nonce until a value is found that gives the block's hash the required number of leading zero bits. Once the hashing has produced a valid result, the block cannot be changed without redoing the work. As later records or "blocks" are chained after it, the work to change the block would include redoing the work for each subsequent block.

Majority consensus in Bitcoin is represented by the longest chain, which required the greatest amount of effort to produce it. If a majority of computing power is controlled by honest nodes, the honest chain will grow fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of that block and all blocks after it and then surpass the work of the honest nodes. The probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.[2]
To compensate for increasing hardware speed and varying interest in running nodes over time, the difficulty of finding a valid hash is adjusted roughly every two weeks. If blocks were generated too quickly, the difficulty increases and more hashes are required to find a block and to generate new bitcoins.[2]
Bitcoin mining is a competitive endeavor. An arms race has been observed through the various hashing technologies that have been used to mine bitcoins: basic CPUs, high-end GPUs (graphics processing units) common in many gaming computers, FPGAs (field-programmable gate arrays) and ASICs (application-specific integrated circuits) all have been used with the latter reducing profitability of each former technology. The newest addition, ASICs, are built into devices that are specialized for Bitcoin mining.[8] As bitcoins become more difficult to mine, computer hardware manufacturing companies have seen an increase in sales of high-end products.[9]
Computing power is often bundled together or "pooled" into a central server to reduce variance in miner income. Individual mining rigs often have to wait relatively long periods of time to confirm a block of transactions and receive payment. When miners cooperate in a pool, all participating miners receive a number of the bitcoins every time a participating server solves a block. This payment is proportional to the amount of work an individual miner contributed to help find that block.[10]
|
Process
A rough overview of the process to mine bitcoins is:[2]
- New transactions are broadcast to all nodes.
- Each miner node collects new transactions into a block.
- Each miner node works on finding a difficult proof-of-work for its block.
- When a node finds a proof-of-work, it broadcasts the block to all nodes.
- New bitcoins are successfully collected or "mined" by the receiving node which found the proof-of-work.
- Nodes accept the block only if all transactions in it are valid and not already spent.
- Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
- Repeat.
Nodes are incentivized to work on extending the longest chain or risk their work being wasted. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. In that case, they work on the first one they received, but save the other branch in case it becomes longer. The tie will be broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one.
New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, however, transactions will get into a block before long. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one.
Mined bitcoins
By convention, the first transaction in a block is a special transaction that produces new bitcoins owned by the creator of the block. This adds an incentive for nodes to support the network,[2] and provides a way to initially distribute coins into circulation, since there is no central authority to issue them.
The continual and steady addition of new coins is analogous to gold miners expending resources to add gold to circulation.[2] In this case, it is computing power and electricity that is expended.
The incentive can also be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction.
Local system resources
Once the latest transaction of a coin is buried under enough blocks, fully spent transactions which preceded it can be discarded in order to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle tree, with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes need not be stored.[1]
A block header with no transactions would be about 80 bytes. Supposing that blocks are generated every 10 minutes, 80 bytes × 6 × 24 × 365 = 4.2 MB per year. With computer systems typically selling with 6 GB of RAM as of 2013, and Moore's law predicting current growth of 1.2 GB per year, storage should not be a problem even if the block headers need to be kept in memory.[1]
Payment verification
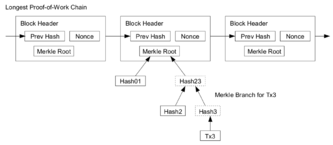
It is possible to verify Bitcoin payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which are available by querying network nodes until it's apparent that the longest chain has been obtained. Then, get the Merkle branch linking the transaction to the block it is timestamped in. One can not check the transaction for oneself, but by linking it to a place in the chain, one can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it.[1]
As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. To protect against this, alerts from network nodes detecting an invalid block prompt the user's software to download the full block and verify alerted transactions to confirm their inconsistency. Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification.[1]
References
- ↑ 1.0 1.1 1.2 1.3 1.4 Nakamoto, Satoshi (24 May 2009). "Bitcoin: A Peer-to-Peer Electronic Cash System". Retrieved 20 December 2012.
- ↑ 2.0 2.1 2.2 2.3 2.4 2.5 2.6 Barber, Simon; Boyen, Xavier; Shi, Elaine and Uzun, Ersin (2012). "Bitter to Better — how to make Bitcoin a better currency". Financial Cryptography and Data Security (Springer Publishing).
- ↑ 1FfmbHfnpaZjKFvyi1okTjJJusN455paPH, Accessed 12-18-2013
- ↑ Grilled cheese meets Bitcoin: Why this food truck is embracing digital currency, GeekWire
- ↑ Trezor Bitcoin Hardware Wallet On Pace for October Deliveries, The Genesis Block
- ↑ "Bitcoin Wiki article on Cold Storage". En.bitcoin.it. 2013-05-26. Retrieved 2013-11-29.
- ↑ Physical Bitcoins by Casascius http://www.casascius.com/
- ↑ Tindell, Ken (5 April 2013). "Geeks Love The Bitcoin Phenomenon Like They Loved The Internet In 1995". Business Insider. Archived from the original on 2013-04-29.
- ↑ 2014-01-04, Bitcoin boom benefiting TSMC: report, Taipei Times
- ↑ Biggs, John (8 April 2013). "How To Mine Bitcoins". Techcrunch. Archived from the original on 2013-04-29.
External links
| |||||||||||||||||||||





