Network Time Protocol
The Network Time Protocol (NTP) is a protocol and software implementation for synchronizing the clocks of computer systems over packet-switched, variable-latency data networks. Originally designed by David L. Mills of the University of Delaware and still maintained by him and a team of volunteers, it was first used before 1985 and is one of the oldest Internet protocols.
NTP is not related to the simpler Daytime Protocol or the Time Protocol.
| Internet protocol suite |
|---|
| Application layer |
| Transport layer |
| Internet layer |
| Link layer |
Contents |
Overview
NTP provides Coordinated Universal Time (UTC) including scheduled leap second adjustments. No information about time zones or daylight saving time is transmitted; this information is outside its scope and must be obtained separately.
NTP uses Marzullo's algorithm and is designed to resist the effects of variable latency. NTP can usually maintain time to within tens of milliseconds over the public Internet,[1] and can achieve 1 millisecond accuracy in local area networks under ideal conditions.[2]
As of June 2010[update], the current reference implementation is version 4 (NTPv4), which is a proposed standard as documented in RFC 5905.
The protocol uses the User Datagram Protocol (UDP) on port number 123.[3]
A less complex implementation of NTP, using the same protocol but without requiring the storage of state over extended periods of time, is known as the Simple Network Time Protocol (SNTP). It is used in some embedded devices and in applications where high accuracy timing is not required (RFC 1361, RFC 1769, RFC 2030, RFC 4330 and RFC 5905).
NTP software implementations
Unix
For modern Unix systems, the NTP client is implemented as a daemon process that runs continuously in user space (ntpd). Because of sensitivity to timing, however, it is important to have the standard NTP clock phase-locked loop implemented in kernel space. All recent versions of Linux, BSD, Mac OS X, Solaris and AIX are implemented in this manner.
The NTP packet is a UDP datagram, carried on port 123.[4]
Microsoft Windows
All Microsoft Windows versions since Windows 2000 include the Windows Time Service,[5] which has the ability to sync the computer clock to an NTP server. However, the version in Windows 2000 only implements Simple NTP, and violates several aspects of the NTP version 3 standard.[6] Beginning with Windows Server 2003, the Microsoft documentation states: "Although the Windows Time service is not an exact implementation of the Network Time Protocol (NTP), it uses the complex suite of algorithms that is defined in the NTP specifications to ensure that clocks on computers throughout a network are as accurate as possible.[7]"
However, the Windows Time Service cannot maintain the system time more accurately than about a 1-2 second range. Microsoft "[does] not guarantee and [does] not support the accuracy of the W32Time service between nodes on a network. The W32Time service is not a full-featured NTP solution that meets time-sensitive application needs. The W32Time service is primarily designed to do the following:[8]
- Make the Kerberos version 5 authentication protocol work.
- Provide loose sync time for client computers."
The reference implementation of NTP can be used on Microsoft Windows NT 4.0 systems.[9]
Clock strata
NTP uses a hierarchical, semi-layered system of levels of clock sources. Each level of this hierarchy is termed a stratum and is assigned a layer number starting with 0 (zero) at the top. The stratum level defines its distance from the reference clock and exists to prevent cyclical dependencies in the hierarchy. It is important to note that the stratum is not an indication of quality or reliability, it is common to find stratum 3 time sources that are higher quality than other stratum 2 time sources. This definition of stratum is also different from the notion of clock strata used in telecommunication systems.
- Stratum 0
- These are devices such as atomic (caesium, rubidium) clocks, GPS clocks or other radio clocks. Stratum-0 devices are traditionally not attached to the network; instead they are locally connected to computers (e.g., via an RS-232 connection using a pulse per second signal).
- Stratum 1
- These are computers attached to Stratum 0 devices. Normally they act as servers for timing requests from Stratum 2 servers via NTP. These computers are also referred to as time servers.
- Stratum 2
- These are computers that send NTP requests to Stratum 1 servers. Normally a Stratum 2 computer will reference a number of Stratum 1 servers and use the NTP algorithm to gather the best data sample, dropping any Stratum 1 servers that seem obviously wrong. Stratum 2 computers will peer with other Stratum 2 computers to provide more stable and robust time for all devices in the peer group. Stratum 2 computers normally act as servers for Stratum 3 NTP requests.
- Stratum 3
- These computers employ exactly the same NTP functions of peering and data sampling as Stratum 2, and can themselves act as servers for lower strata. NTP (depending on what version of NTP protocol in use) supports up to 256 strata.
NTP timestamps
The 64-bit timestamps used by NTP consist of a 32-bit seconds part and a 32-bit fractional second part, giving NTP a time scale that rolls over every 232 seconds (136 years) and a theoretical resolution of 2−32 seconds (233 picoseconds). NTP uses an epoch of January 1, 1900. The first rollover will occur in 2036, prior to the UNIX year 2038 problem.
Implementations should disambiguate NTP time using a knowledge of the approximate time from other sources. Since NTP only works with the differences between timestamps and never their absolute values, the wraparound is invisible as long as the timestamps are within 68 years of each other. This means that the rollover will be invisible for most running systems, since they will have the correct time to within a very small tolerance. However, systems that are starting up need to know the date within no more than 68 years. Given the large allowed error, it is not expected that this is too onerous a requirement. One suggested method is to set the clock to no earlier than the system build date. Many systems use a battery powered hardware clock to avoid this problem.
Even so, future versions of NTP may extend the time representation to 128 bits: 64 bits for the second and 64 bits for the fractional-second. The current NTP4 format has support for Era Number and Era Offset, that when used properly should aid fixing date rollover issues until NTP5 replaces NTP4. According to Mills, "The 64 bit value for the fraction is enough to resolve the amount of time it takes a photon to pass an electron at the speed of light. The 64 bit second value is enough to provide unambiguous time representation until the universe goes dim."[10][note 1]
Clock synchronization algorithm
To synchronize its clock with a remote server, the NTP client must compute the round-trip delay time and the offset. The round-trip delay is computed as 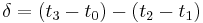 , where
, where 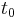 is the time of the request packet transmission,
is the time of the request packet transmission, 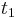 is the time of the request packet reception,
is the time of the request packet reception, 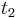 is the time of the response packet transmission and
is the time of the response packet transmission and 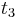 is the time of the response packet reception.
is the time of the response packet reception.  is the time elapsed on the client side between the emission of the request packet and the reception of the response packet, while
is the time elapsed on the client side between the emission of the request packet and the reception of the response packet, while  is the time the server waited before sending the answer. The offset is given by
is the time the server waited before sending the answer. The offset is given by 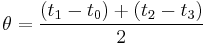 .[11]
.[11]
The NTP synchronization is correct when both the incoming and outgoing routes between the client and the server have symmetrical nominal delay. If the routes do not have a common nominal delay, the synchronization has a systematic bias of half the difference between the forward and backward travel times.[12]
Leap seconds
NTP delivers UTC time. UTC is subject to scheduled leap seconds to synchronize the timescale to the rotation of the earth. When a leap second is added, NTP is suspended for 1 second. Because NTP has no mechanism for remembering the history of leap seconds, leap seconds cause the entire NTP timescale to shift by 1 second.[13][14]
Security concerns
Only a few security problems have been identified in the reference implementation of the NTP codebase in its 25+ year history.[15][16] The protocol has been undergoing revision and review over its entire history; no security vulnerabilities have ever been reported that have been traced to the NTP specification.[17] The current codebase for the reference implementation has been undergoing security audits from several sources for several years now, and there are no known high-risk vulnerabilities in the current released software.[18]
See also
- Allan variance
- Clock synchronization
- International Atomic Time
- ntpd, OpenNTPD and Ntpdate
- NTP pool, a collection of worldwide computers that provide a highly accurate time via the Network Time Protocol
- NTP server misuse and abuse
- Synchronization
- Time server
- NITZ (Network Identity and Time Zone) a mechanism for provisioning local time and date, as well as network provider identity information to mobile devices via a wireless network
Other time synchronization protocols:
- DAYTIME protocol, older time synchronization protocol using TCP or UDP port 13
- ICMP Timestamp and ICMP Timestamp Reply, older time synchronization protocol using ICMP
- Precision Time Protocol, a high-precision protocol for use on local area networks
- Time Protocol, older time synchronization protocol using TCP or UDP port 37
Notes
- ^ 2−64 seconds is about 54 zeptoseconds (light would travel 16.26 picometres, or approximately 0.31 × Bohr radius ), and 264 seconds is about 585 billion years.
References
- ^ "Executive Summary: Computer Network Time Synchronization". http://www.eecis.udel.edu/~mills/exec.html. Retrieved 2011-11-21.
- ^ "NTP FAQ". The NTP Project. http://www.ntp.org/ntpfaq/NTP-s-algo.htm#Q-ACCURATE-CLOCK. Retrieved 2011-08-27.
- ^ "Port Numbers". The Internet Assigned Numbers Authority (IANA). http://www.iana.org/assignments/port-numbers.
- ^ http://tools.ietf.org/html/rfc5905 Page 16
- ^ "Windows Time Service Technical Reference". technet.microsoft.com. 2011-08-17. http://technet.microsoft.com/en-us/library/cc773061%28WS.10%29.aspx. Retrieved 2011-09-19.
- ^ "Windows Time Service page at NTP.org". Support.ntp.org. 2008-02-25. http://support.ntp.org/bin/view/Support/WindowsTimeService. Retrieved 2011-01-12.
- ^ "How the Windows Time Service Works". technet.microsoft.com. 2010-03-12. http://technet.microsoft.com/en-us/library/cc773013%28WS.10%29.aspx. Retrieved 2011-09-19.
- ^ "Support boundary to configure the Windows Time service for high accuracy environments". Support.microsoft.com. 2010-02-02. http://support.microsoft.com/kb/939322. Retrieved 2011-01-12.
- ^ "NTP 4.x for Windows NT". NTP Documentation Archive. http://doc.ntp.org/4.2.6/hints/winnt.html. Retrieved 2011-01-12.
- ^ University of Delaware Digital Systems Seminar presentation by David Mills, 2006-04-26
- ^ Mills, David L. (2005), NTP Clock Discipline Modelling and Analysis, p. 10, http://www.eecis.udel.edu/~mills/database/brief/algor/algor.pdf, retrieved 2011-07-13
- ^ Gotoh, T; Imamura, K; Kaneko, A (2002). "Improvement of NTP time offset under the asymmetric network with double packets method". pp. 448–449. doi:10.1109/CPEM.2002.1034915. http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=1034915&userType=inst
- ^ David Mills. "The NTP Timescale and Leap Seconds". http://www.eecis.udel.edu/~mills/leap.html. Retrieved 2011-09-15.
- ^ David Mills. "NTP Timescale and Leap Seconds". http://doc.ntp.org/4.1.2/leap.htm. Retrieved 2011-09-15.
- ^ "Security Notice". Support.ntp.org. 2009-12-10. http://support.ntp.org/security. Retrieved 2011-01-12.
- ^ results returned by a search on "Network Time Protocol" at http://cert.org]
- ^ Look at RFC 778, RFC 891, RFC 956, RFC 958, RFC 1305, RFC 5905, and the NTPv4 specification and notice the lack of revisions due to protocol security problems. Similarly, look at the results returned by a search on "Network Time Protocol" at http://cert.org]
- ^ "Code Audit". Support.ntp.org. 2009-06-13. http://support.ntp.org/Main/CodeAudit. Retrieved 2011-01-12.
Further reading
- Mills, David L.. Computer Network Time Synchronization: The Network Time Protocol. Taylor & Francis / CRC Press. ISBN 0849358051.
External links
- Official site
- NTP Public Services Project This is the home for the NTP (Network Time Protocol) Public Services Project that provides public support for the NTP Project and the IETF NTP Working Group. Also a Wiki with lists of NTP servers.
- Pool of public NTP Time Servers
- For a comprehensive list of NTP Servers
- IETF NTP working group
- David Mills' NTP project page
- Time and NTP paper
- NTP Survey 2005